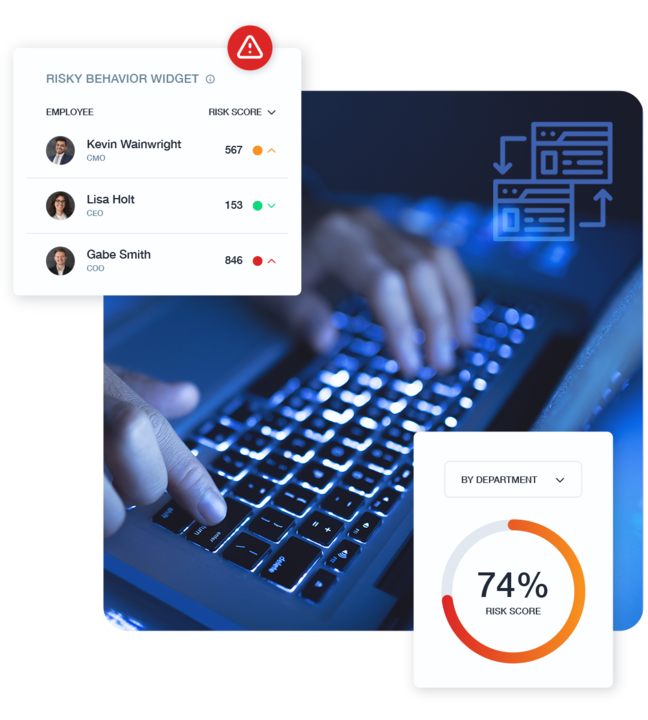
Strengthen Your Cybersecurity with Teramind DLP
Meet NIST CSF 2.0 Tier 4 Compliance Requirements
The latest NIST Cybersecurity Framework (CSF) 2.0 mandates robust data protection measures for government agencies and contractors. Teramind’s Data Loss Prevention (DLP) solution simplifies compliance, providing a quick and cost-effective way to meet these requirements while enhancing your organization’s cybersecurity posture.
.elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block}
Achieve NIST Compliance Across Key Requirements
Teramind DLP empowers government organizations to align with NIST CSF 2.0 standards through advanced user behavior analytics and robust data protection tools. Here’s how we address each critical requirement:
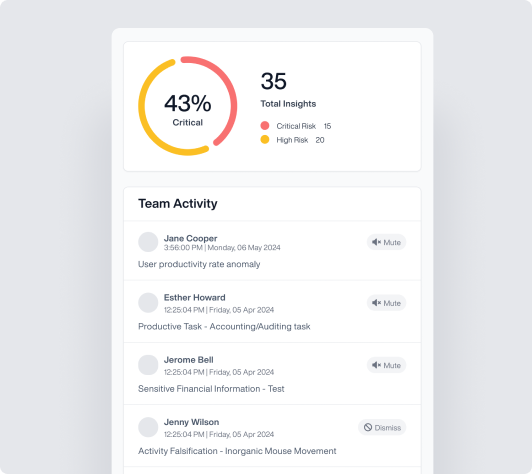
IDENTIFY-P: Manage Privacy Risks Effectively
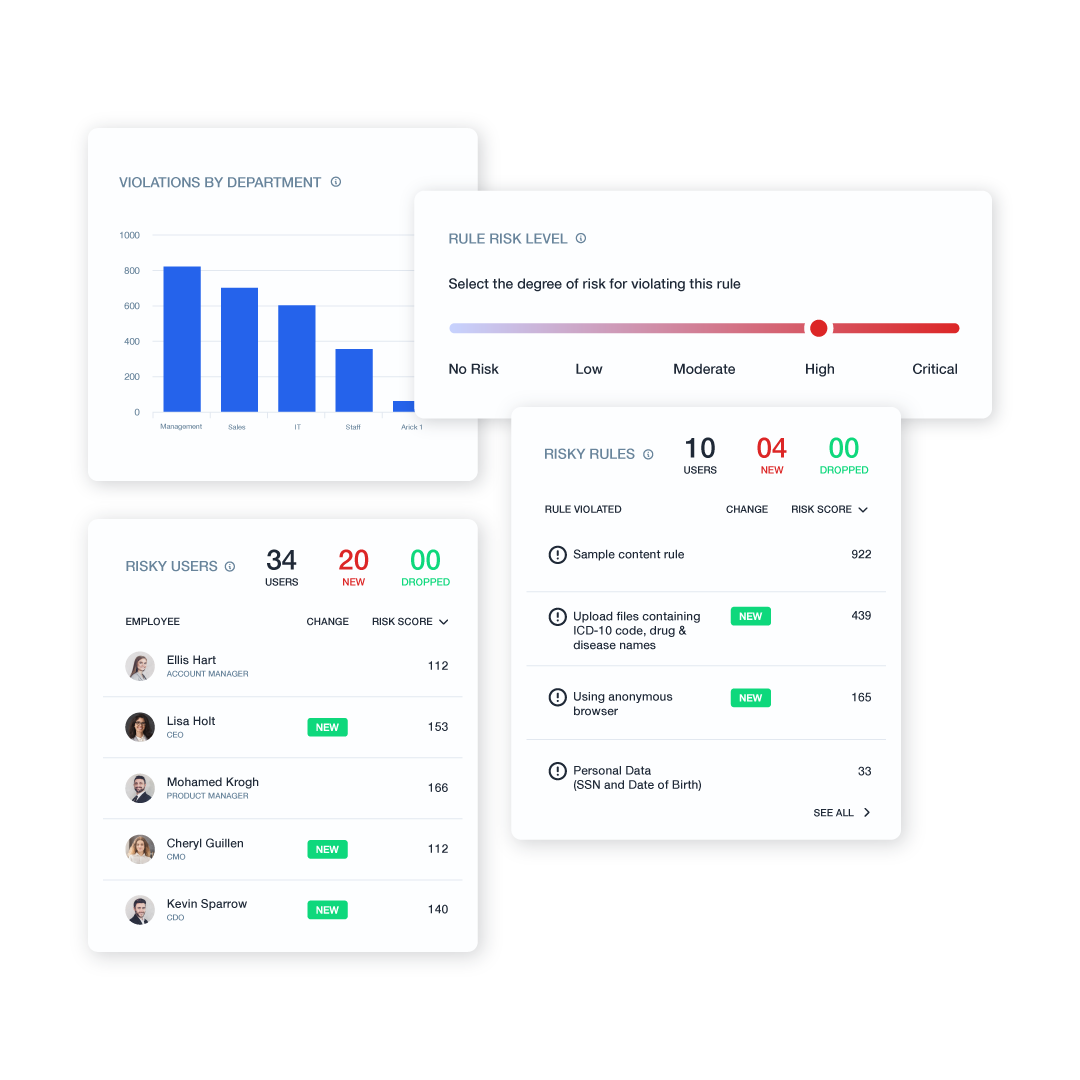
- Data Discovery and Classification: Locate sensitive data across endpoints, networks, and the cloud.
- Risk Identification: Uncover data usage patterns and potential vulnerabilities to proactively manage privacy risks.
GOVERN-P: Establish Comprehensive Governance
- Policy Enforcement & Reporting: Implement real-time monitoring and detailed reporting for NIST-aligned compliance.
- Audit Trails: Transparent logging of all data activities for a clear compliance audit trail.
- Role-Based Access Control (RBAC): Ensure only authorized personnel access sensitive data.
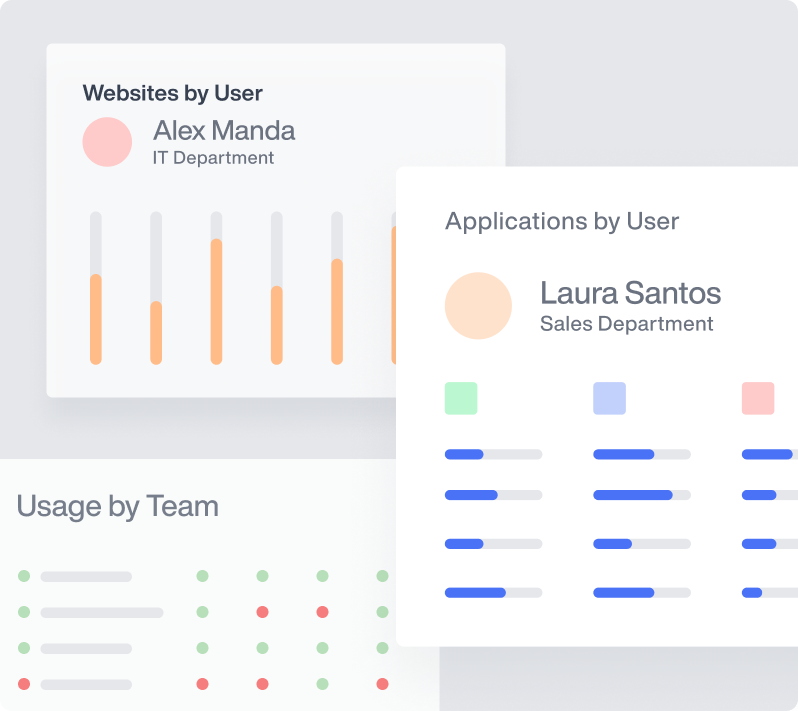
CONTROL-P: Manage Data Access with Precision
- Granular Access Control: Define and enforce policies tailored to your organization’s needs.
- Data Masking & Redaction: Protect sensitive information by limiting visibility to unauthorized users.
- Behavioral Monitoring: Detect and prevent unauthorized data access and potential breaches.
COMMUNICATE-P: Foster Transparency and Awareness
- Employee Training & Awareness: Automated alerts and training modules to educate teams on proper data handling.
- Incident Communication: Clear workflows for addressing privacy violations and maintaining trust.

PROTECT-P: Safeguard Sensitive Data
- Real-Time Monitoring & Alerts: Block unauthorized data exfiltration before it happens.
- Data Encryption: Secure data in transit and at rest with advanced encryption protocols.
- DLP Policies: Prevent data from being shared with unapproved destinations or users.
Try Platform
With a Live Demo
to see how it works.

Why Teramind
With Teramind DLP, compliance isn’t just a checkbox; it’s a transformative step toward comprehensive cybersecurity. Our solution is quick to implement, cost-effective, and tailored to meet the evolving needs of government agencies under NIST CSF 2.0 guidelines.
max-width:140px;
}/* End custom CSS */
/* Start custom CSS for image, class: .elementor-element-4fd823f */.award-hover-image{
max-width:140px!important;
}/* End custom CSS */
What our Customers Say
.elementor-widget-image-box .elementor-image-box-content{width:100%}@media (min-width:768px){.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper,.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{display:flex}.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{text-align:end;flex-direction:row-reverse}.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper{text-align:start;flex-direction:row}.elementor-widget-image-box.elementor-position-top .elementor-image-box-img{margin:auto}.elementor-widget-image-box.elementor-vertical-align-top .elementor-image-box-wrapper{align-items:flex-start}.elementor-widget-image-box.elementor-vertical-align-middle .elementor-image-box-wrapper{align-items:center}.elementor-widget-image-box.elementor-vertical-align-bottom .elementor-image-box-wrapper{align-items:flex-end}}@media (max-width:767px){.elementor-widget-image-box .elementor-image-box-img{margin-left:auto!important;margin-right:auto!important;margin-bottom:15px}}.elementor-widget-image-box .elementor-image-box-img{display:inline-block}.elementor-widget-image-box .elementor-image-box-title a{color:inherit}.elementor-widget-image-box .elementor-image-box-wrapper{text-align:center}.elementor-widget-image-box .elementor-image-box-description{margin:0}
Larissa H.
IT Support Specialist
Yakir D.
CIO
IT Security & Risk Manager
$7B Manufacturing Enterprise
The post NIST Landing Page first appeared on Teramind.
Source: itsecuritycentral.teramind.co

