.elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px}
Software Usage Tracking That Keeps Your Team Productive & Secure
.elementor-widget-text-editor.elementor-drop-cap-view-stacked .elementor-drop-cap{background-color:#69727d;color:#fff}.elementor-widget-text-editor.elementor-drop-cap-view-framed .elementor-drop-cap{color:#69727d;border:3px solid;background-color:transparent}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap{margin-top:8px}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap-letter{width:1em;height:1em}.elementor-widget-text-editor .elementor-drop-cap{float:left;text-align:center;line-height:1;font-size:50px}.elementor-widget-text-editor .elementor-drop-cap-letter{display:inline-block}
Keep employee productivity high and security risks low with comprehensive software usage monitoring. Track software activity, detect unauthorized applications, identify suspicious behavior patterns, and gain team-wide visibility into digital workflows.
.elementor-widget-video .elementor-widget-container{overflow:hidden;transform:translateZ(0)}.elementor-widget-video .elementor-wrapper{aspect-ratio:var(–video-aspect-ratio)}.elementor-widget-video .elementor-wrapper iframe,.elementor-widget-video .elementor-wrapper video{height:100%;width:100%;display:flex;border:none;background-color:#000}@supports not (aspect-ratio:1/1){.elementor-widget-video .elementor-wrapper{position:relative;overflow:hidden;height:0;padding-bottom:calc(100% / var(–video-aspect-ratio))}.elementor-widget-video .elementor-wrapper iframe,.elementor-widget-video .elementor-wrapper video{position:absolute;top:0;right:0;bottom:0;left:0}}.elementor-widget-video .elementor-open-inline .elementor-custom-embed-image-overlay{position:absolute;top:0;right:0;bottom:0;left:0;background-size:cover;background-position:50%}.elementor-widget-video .elementor-custom-embed-image-overlay{cursor:pointer;text-align:center}.elementor-widget-video .elementor-custom-embed-image-overlay:hover .elementor-custom-embed-play i{opacity:1}.elementor-widget-video .elementor-custom-embed-image-overlay img{display:block;width:100%;aspect-ratio:var(–video-aspect-ratio);-o-object-fit:cover;object-fit:cover;-o-object-position:center center;object-position:center center}@supports not (aspect-ratio:1/1){.elementor-widget-video .elementor-custom-embed-image-overlay{position:relative;overflow:hidden;height:0;padding-bottom:calc(100% / var(–video-aspect-ratio))}.elementor-widget-video .elementor-custom-embed-image-overlay img{position:absolute;top:0;right:0;bottom:0;left:0}}.elementor-widget-video .e-hosted-video .elementor-video{-o-object-fit:cover;object-fit:cover}.e-con-inner>.elementor-widget-video,.e-con>.elementor-widget-video{width:var(–container-widget-width);–flex-grow:var(–container-widget-flex-grow)}
.elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block}

Why Choose Teramind’s Software Usage Tracking
Real-Time Visibility & Insights
.elementor-widget-divider{–divider-border-style:none;–divider-border-width:1px;–divider-color:#0c0d0e;–divider-icon-size:20px;–divider-element-spacing:10px;–divider-pattern-height:24px;–divider-pattern-size:20px;–divider-pattern-url:none;–divider-pattern-repeat:repeat-x}.elementor-widget-divider .elementor-divider{display:flex}.elementor-widget-divider .elementor-divider__text{font-size:15px;line-height:1;max-width:95%}.elementor-widget-divider .elementor-divider__element{margin:0 var(–divider-element-spacing);flex-shrink:0}.elementor-widget-divider .elementor-icon{font-size:var(–divider-icon-size)}.elementor-widget-divider .elementor-divider-separator{display:flex;margin:0;direction:ltr}.elementor-widget-divider–view-line_icon .elementor-divider-separator,.elementor-widget-divider–view-line_text .elementor-divider-separator{align-items:center}.elementor-widget-divider–view-line_icon .elementor-divider-separator:after,.elementor-widget-divider–view-line_icon .elementor-divider-separator:before,.elementor-widget-divider–view-line_text .elementor-divider-separator:after,.elementor-widget-divider–view-line_text .elementor-divider-separator:before{display:block;content:””;border-block-end:0;flex-grow:1;border-block-start:var(–divider-border-width) var(–divider-border-style) var(–divider-color)}.elementor-widget-divider–element-align-left .elementor-divider .elementor-divider-separator>.elementor-divider__svg:first-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-left .elementor-divider-separator:before{content:none}.elementor-widget-divider–element-align-left .elementor-divider__element{margin-left:0}.elementor-widget-divider–element-align-right .elementor-divider .elementor-divider-separator>.elementor-divider__svg:last-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-right .elementor-divider-separator:after{content:none}.elementor-widget-divider–element-align-right .elementor-divider__element{margin-right:0}.elementor-widget-divider–element-align-start .elementor-divider .elementor-divider-separator>.elementor-divider__svg:first-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-start .elementor-divider-separator:before{content:none}.elementor-widget-divider–element-align-start .elementor-divider__element{margin-inline-start:0}.elementor-widget-divider–element-align-end .elementor-divider .elementor-divider-separator>.elementor-divider__svg:last-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-end .elementor-divider-separator:after{content:none}.elementor-widget-divider–element-align-end .elementor-divider__element{margin-inline-end:0}.elementor-widget-divider:not(.elementor-widget-divider–view-line_text):not(.elementor-widget-divider–view-line_icon) .elementor-divider-separator{border-block-start:var(–divider-border-width) var(–divider-border-style) var(–divider-color)}.elementor-widget-divider–separator-type-pattern{–divider-border-style:none}.elementor-widget-divider–separator-type-pattern.elementor-widget-divider–view-line .elementor-divider-separator,.elementor-widget-divider–separator-type-pattern:not(.elementor-widget-divider–view-line) .elementor-divider-separator:after,.elementor-widget-divider–separator-type-pattern:not(.elementor-widget-divider–view-line) .elementor-divider-separator:before,.elementor-widget-divider–separator-type-pattern:not([class*=elementor-widget-divider–view]) .elementor-divider-separator{width:100%;min-height:var(–divider-pattern-height);-webkit-mask-size:var(–divider-pattern-size) 100%;mask-size:var(–divider-pattern-size) 100%;-webkit-mask-repeat:var(–divider-pattern-repeat);mask-repeat:var(–divider-pattern-repeat);background-color:var(–divider-color);-webkit-mask-image:var(–divider-pattern-url);mask-image:var(–divider-pattern-url)}.elementor-widget-divider–no-spacing{–divider-pattern-size:auto}.elementor-widget-divider–bg-round{–divider-pattern-repeat:round}.rtl .elementor-widget-divider .elementor-divider__text{direction:rtl}.e-con-inner>.elementor-widget-divider,.e-con>.elementor-widget-divider{width:var(–container-widget-width,100%);–flex-grow:var(–container-widget-flex-grow)}
Enterprise-grade monitoring provides complete visibility into which applications your team uses, when they use them, and how they interact with critical software tools.
Advanced Security Protection
Sophisticated threat detection identifies unauthorized applications and suspicious usage patterns before they can compromise your sensitive data or systems.
Productivity-Focused Analytics
Data-driven insights reveal productivity trends, workflow bottlenecks, and optimization opportunities to help your team work more effectively.
Productivity Intelligence
Transform usage data into actionable workflow and process improvements.
- Time Allocation Analysis: See exactly where time is spent across applications with granular timestamps and duration metrics that help identify resource-intensive processes and bottlenecks in your workflow.
- Focus Metrics: Track context switching and application hopping that kills productivity by identifying when users jump between too many apps and quantifying their focus sessions.
- Efficiency Indicators: Spot redundant processes when users toggle between multiple tools to accomplish a single task, helping streamline workflows and identify automation opportunities.
- Productivity Benchmarking: Overlay usage patterns from your top performers against struggling team members to clone best practices and quickly identify targeted training opportunities.
Behavioral Analytics
Understand user interactions with applications for improved workflow and process design.
- Application Interaction Mapping: Visualize user workflows with heat-mapped process flows showing how users navigate between applications, revealing inefficient paths and integration opportunities.
- Skill Gap Detection: Identify users spending 2-3x longer in applications than their peers to pinpoint where targeted training can deliver immediate productivity gains.
- Feature Utilization: Discover which premium features your team actually uses versus expensive capabilities sitting idle, providing essential data for right-sizing licenses and planning training.
- Adoption Tracking: Monitor the rollout of new tools with adoption velocity metrics showing both usage frequency and depth to help prevent expensive software investments from becoming shelfware.
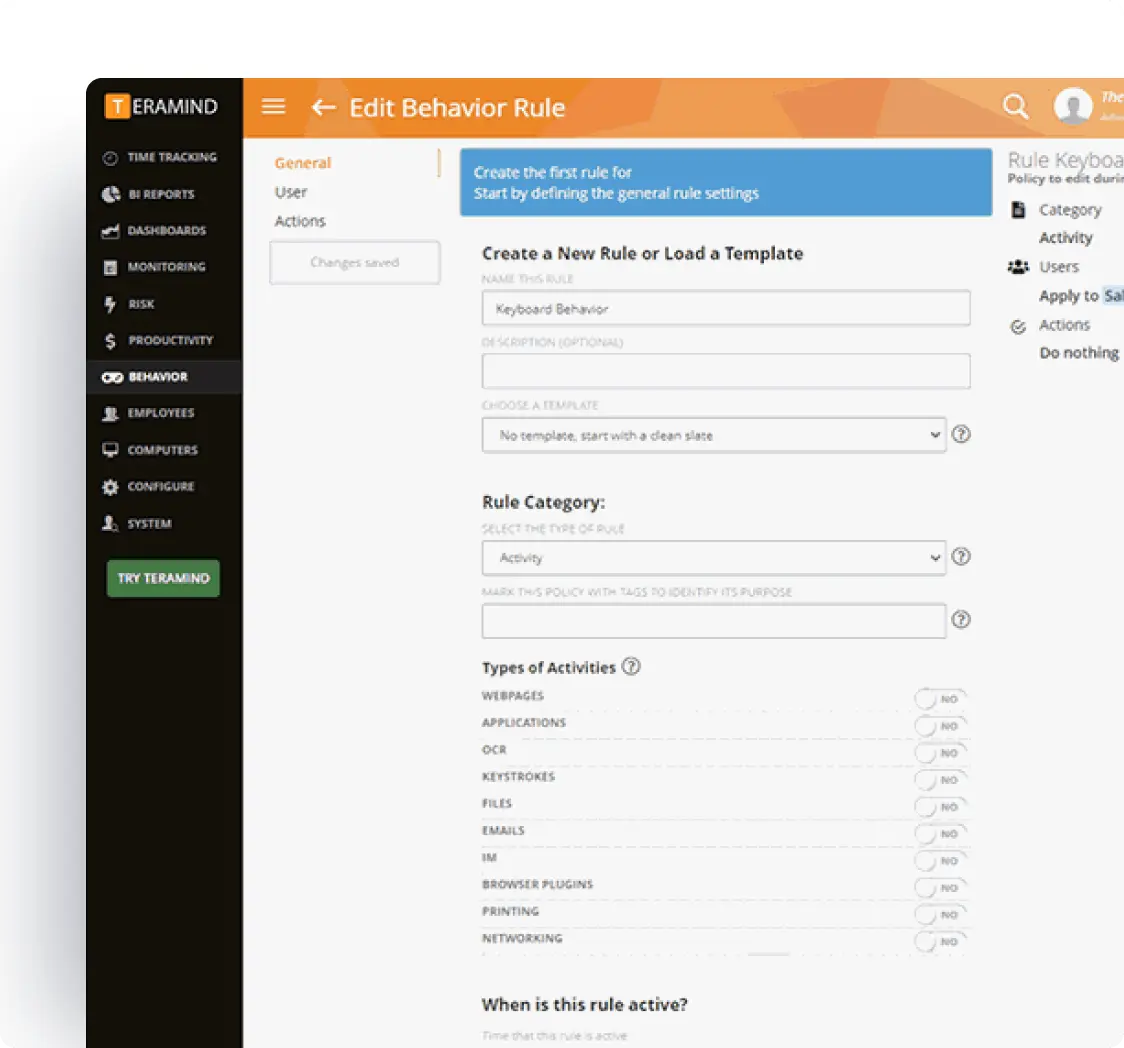
Security & Risk Monitoring
Protect your organization from software-based insider threats and vulnerabilities.
- Unauthorized Application Alerts: Get instant notifications when unapproved software appears on your network, eliminating the delay between installation and detection that leaves your systems vulnerable.
- Behavioral Anomalies: Leverage ML-powered analysis to flag when users access applications at unusual times or in unusual patterns, often the first indicator of insider threats.
- Data Transfer Monitoring: Track file transfers, uploads, and downloads across all monitored applications to prevent data exfiltration through cloud storage, email or messaging apps.
- Application Alerts: Configure application-specific alerts can be set to notify administrators of potential security risks
Shadow IT Management
Discover and secure unauthorized software across your environment.
- Insider Risk Evaluation: Identify potential data exposure vectors when employees use unsanctioned cloud storage, messaging, or file sharing applications outside your security perimeter.
- Policy Enforcement: Deploy automated responses when unauthorized software is detected, from simple alerts to automated removal based on customizable risk thresholds you control.
- Usage Pattern Correlation: Analyze which teams and departments gravitate toward specific unauthorized tools to uncover workflow inefficiencies or gaps in your approved software portfolio.
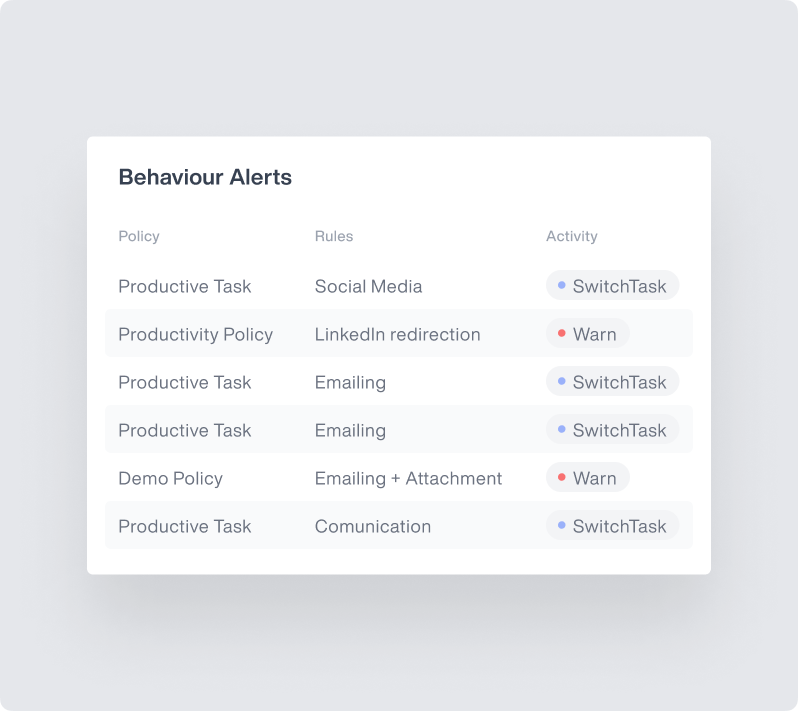
Advanced Reporting & Alerts
Transform usage data into actionable intelligence.
- Custom Dashboards: Build role-specific views to create security-focused dashboards for your SOC team while delivering productivity metrics to department managers.
- Threshold Alerts: Set custom triggers based on any metric combination to get notifications when users spend too much time in non-productive apps or when critical applications show unusual access patterns.
- Trend Analysis: Access historical data with a data warehouse to run custom queries against months of application usage data and identify seasonal patterns and long-term shifts in tool utilization.
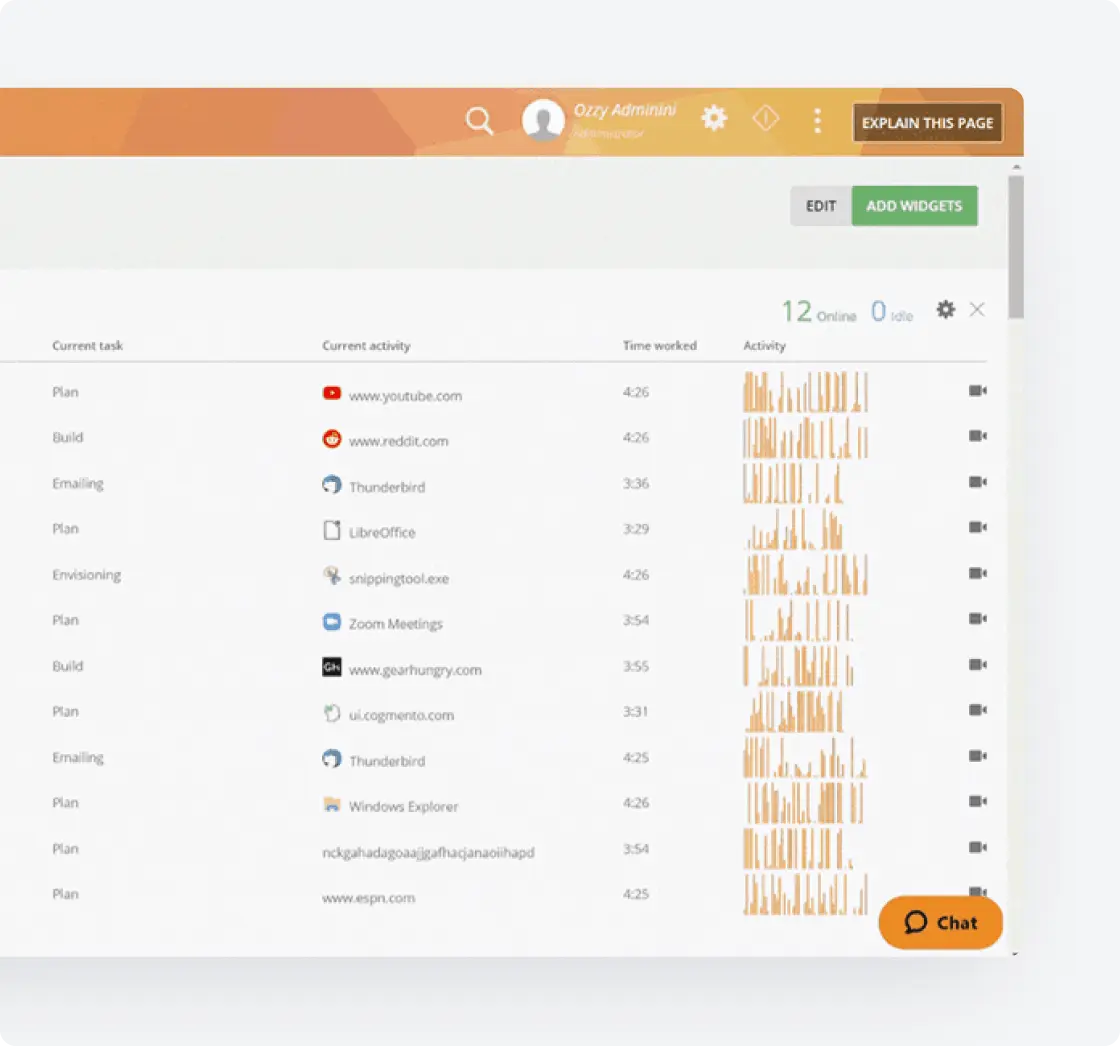
Compliance & Controls
Maintain regulatory compliance and demonstrate due diligence.
- Audit-Ready Documentation: Generate comprehensive reports of all software usage across your organization to provide auditors with evidence of monitoring and control mechanisms.
- Behavior-Based Compliance: Monitor user actions within applications to ensure sensitive data handling follows regulatory requirements and internal governance policies.
- Violation Evidence Collection: Automatically capture and preserve contextual information when policy violations occur to support proper incident investigation and risk management processes.
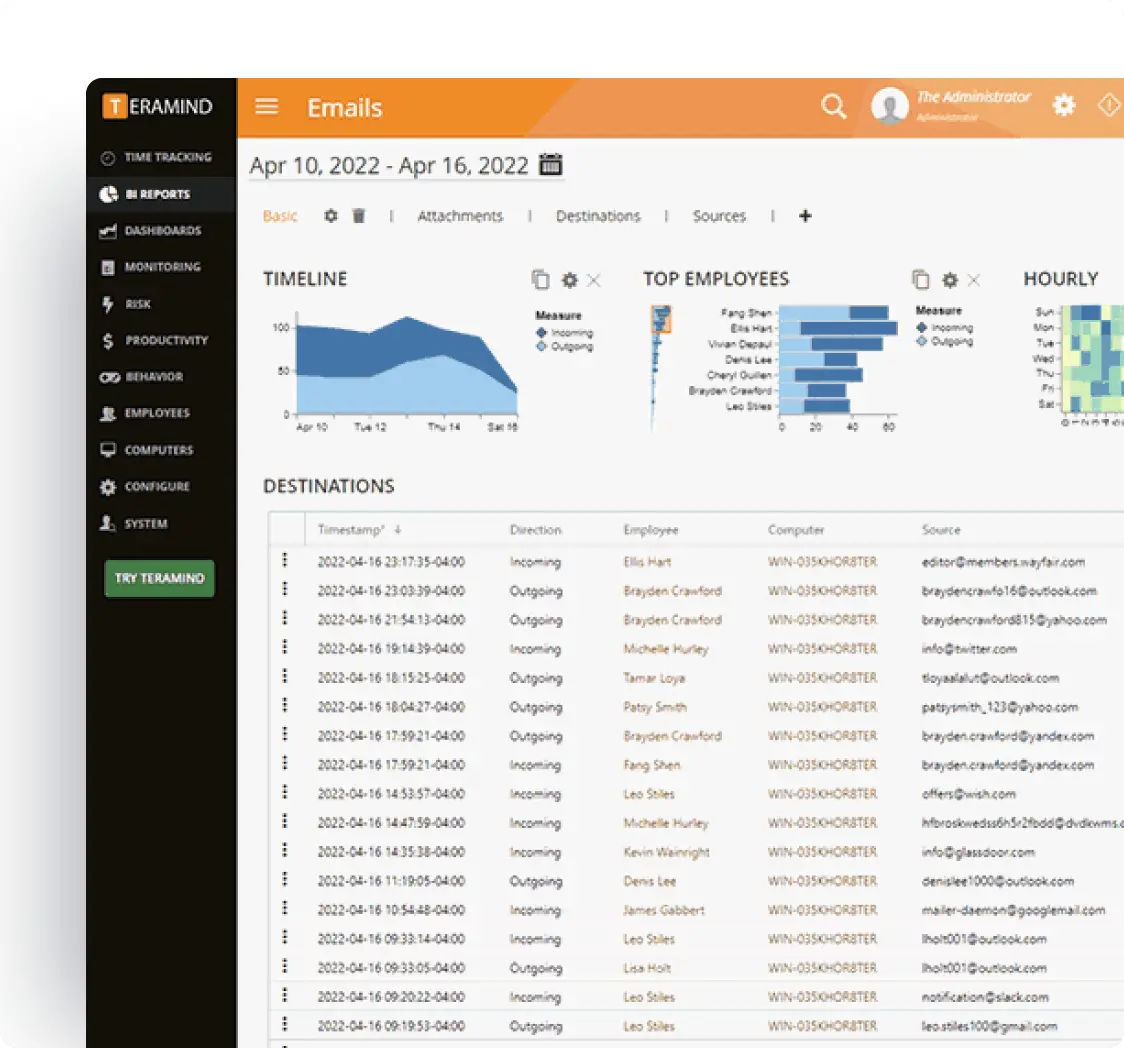
Core Teramind Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
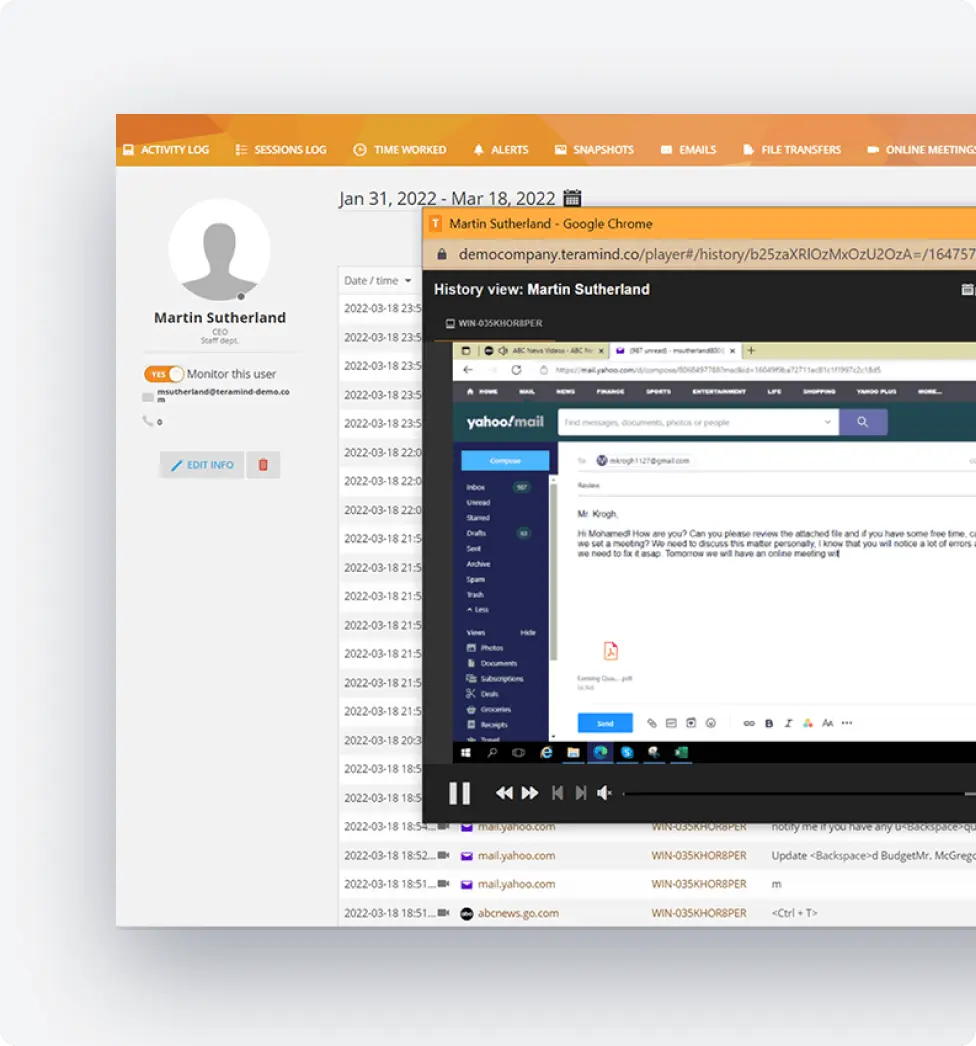
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
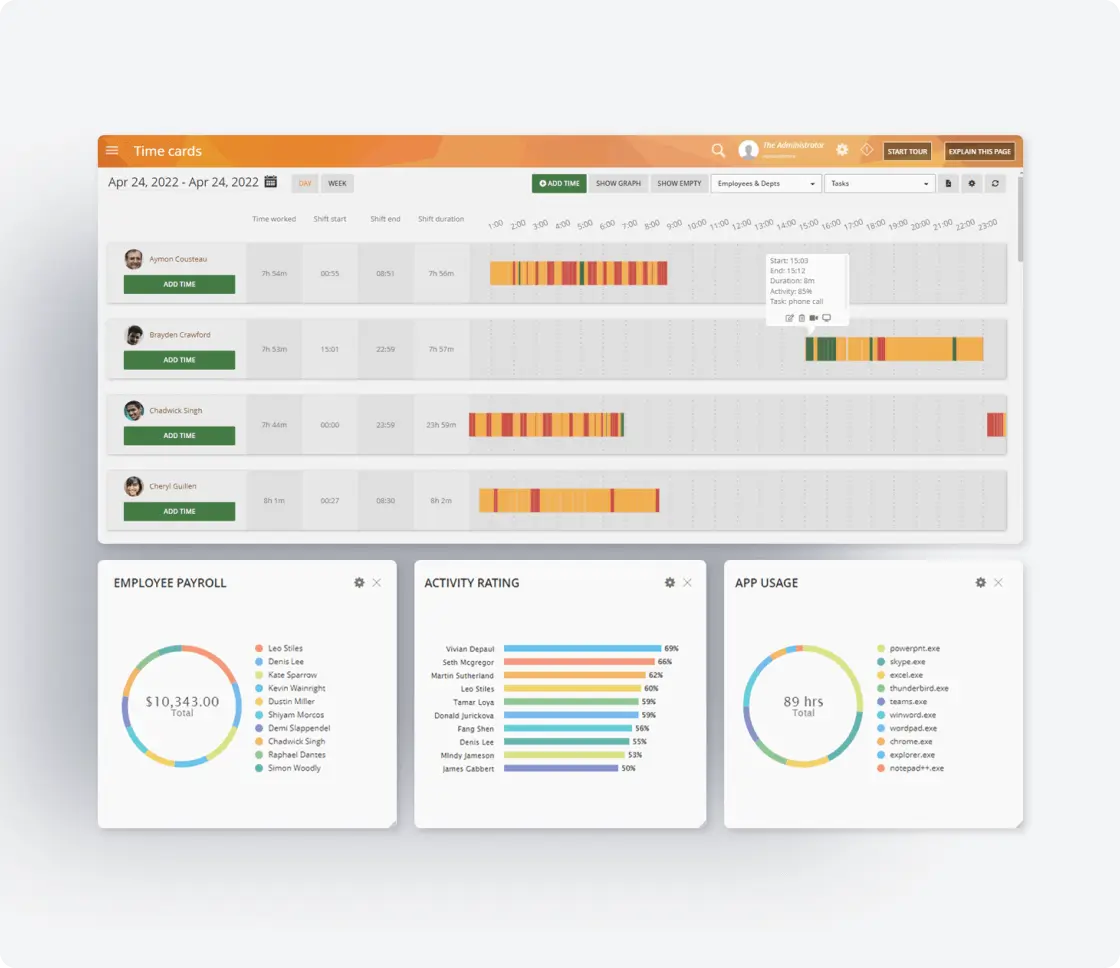
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
.elementor-widget-image-box .elementor-image-box-content{width:100%}@media (min-width:768px){.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper,.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{display:flex}.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{text-align:end;flex-direction:row-reverse}.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper{text-align:start;flex-direction:row}.elementor-widget-image-box.elementor-position-top .elementor-image-box-img{margin:auto}.elementor-widget-image-box.elementor-vertical-align-top .elementor-image-box-wrapper{align-items:flex-start}.elementor-widget-image-box.elementor-vertical-align-middle .elementor-image-box-wrapper{align-items:center}.elementor-widget-image-box.elementor-vertical-align-bottom .elementor-image-box-wrapper{align-items:flex-end}}@media (max-width:767px){.elementor-widget-image-box .elementor-image-box-img{margin-left:auto!important;margin-right:auto!important;margin-bottom:15px}}.elementor-widget-image-box .elementor-image-box-img{display:inline-block}.elementor-widget-image-box .elementor-image-box-title a{color:inherit}.elementor-widget-image-box .elementor-image-box-wrapper{text-align:center}.elementor-widget-image-box .elementor-image-box-description{margin:0}
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
.elementor-widget-table-of-contents .elementor-toc__header-title{color:var(–header-color)}.elementor-widget-table-of-contents.elementor-toc–collapsed .elementor-toc__toggle-button–collapse,.elementor-widget-table-of-contents:not(.elementor-toc–collapsed) .elementor-toc__toggle-button–expand{display:none}.elementor-widget-table-of-contents .elementor-widget-container{min-height:var(–box-min-height);border:var(–box-border-width,1px) solid var(–box-border-color,#9da5ae);border-radius:var(–box-border-radius,3px);background-color:var(–box-background-color);transition:min-height .4s;overflow:hidden}.elementor-toc__header{display:flex;align-items:center;justify-content:space-between;padding:var(–box-padding,20px);background-color:var(–header-background-color);border-bottom:var(–separator-width,1px) solid var(–box-border-color,#9da5ae)}.elementor-toc__header-title{font-size:18px;margin:0;color:var(–header-color);flex-grow:1}.elementor-toc__toggle-button{cursor:pointer;display:inline-flex}.elementor-toc__toggle-button i{color:var(–toggle-button-color)}.elementor-toc__toggle-button svg{height:1em;width:1em;fill:var(–toggle-button-color)}.elementor-toc__spinner-container{text-align:center}.elementor-toc__spinner{font-size:2em}.elementor-toc__spinner.e-font-icon-svg{height:1em;width:1em}.elementor-toc__body{padding:var(–box-padding,20px);max-height:var(–toc-body-max-height);overflow-y:auto}.elementor-toc__body::-webkit-scrollbar{width:7px}.elementor-toc__body::-webkit-scrollbar-thumb{background-color:#babfc5;border-radius:10px}.elementor-toc__list-wrapper{list-style:none;padding:0}.elementor-toc__list-item{margin-bottom:.5em}.elementor-toc__list-item.elementor-item-active{font-weight:700}.elementor-toc__list-item .elementor-toc__list-wrapper{margin-top:.5em;margin-inline-start:var(–nested-list-indent,1em)}.elementor-toc__list-item-text{transition-duration:var(–item-text-transition-duration)}.elementor-toc__list-item-text:hover{color:var(–item-text-hover-color);-webkit-text-decoration:var(–item-text-hover-decoration);text-decoration:var(–item-text-hover-decoration)}.elementor-toc__list-item-text.elementor-item-active{color:var(–item-text-active-color);-webkit-text-decoration:var(–item-text-active-decoration);text-decoration:var(–item-text-active-decoration)}.elementor-toc__list-item-text-wrapper{display:flex;align-items:center}.elementor-toc__list-item-text-wrapper:before,.elementor-toc__list-item-text-wrapper i{margin-inline-end:8px;color:var(–marker-color)}.elementor-toc__list-item-text-wrapper svg{margin-inline-end:8px;fill:var(–marker-color);height:var(–marker-size,.5em);width:var(–marker-size,.5em)}.elementor-toc__list-item-text-wrapper i{font-size:var(–marker-size,.5em)}.elementor-toc__list-item-text-wrapper:before{font-size:var(–marker-size,1em)}.elementor-toc–content-ellipsis .elementor-toc__list-item-text{white-space:nowrap;overflow:hidden;text-overflow:ellipsis}.elementor-toc__list-items–collapsible>.elementor-toc__list-wrapper>.elementor-toc__list-item>.elementor-toc__list-wrapper{display:none}.elementor-toc__heading-anchor{position:absolute}.elementor-toc__body .elementor-toc__list-item-text{color:var(–item-text-color);-webkit-text-decoration:var(–item-text-decoration);text-decoration:var(–item-text-decoration);transition-duration:var(–item-text-transition-duration)}.elementor-toc__body .elementor-toc__list-item-text:hover{color:var(–item-text-hover-color);-webkit-text-decoration:var(–item-text-hover-decoration);text-decoration:var(–item-text-hover-decoration)}.elementor-toc__body .elementor-toc__list-item-text.elementor-item-active{color:var(–item-text-active-color);-webkit-text-decoration:var(–item-text-active-decoration);text-decoration:var(–item-text-active-decoration)}ol.elementor-toc__list-wrapper{counter-reset:item}ol.elementor-toc__list-wrapper .elementor-toc__list-item{counter-increment:item}ol.elementor-toc__list-wrapper .elementor-toc__list-item-text-wrapper:before{content:counters(item,”.”) “. “}
Software Usage Tracking: The Ultimate Guide to User Analytics in 2025
Software usage tracking lets companies see exactly how their teams use different software applications and digital tools throughout the workday. You can track everything from login times and feature usage to workflow patterns and user behavior.
Managers can spot which software features are most valuable, where employees get stuck in their workflows, and which tools might be completely unnecessary.
When you understand these patterns, you can make smarter and more informed decisions about your software investments, provide better training where needed, and fix inefficient processes that slow your team down.
Benefits of Monitoring Software Usage
You might think your team is using all the right tools—but are they actually helping, or just getting in the way? Without software usage monitoring, you’re left guessing. You could be wasting money on unused apps, slowing teams down with clunky software, or missing chances to improve efficiency.
Below, we’ll break down the biggest benefits of software usage monitoring and how it can transform the way your business operates.
Detect Shadow IT and reducing security risks
Shadow IT can be a massive blind spot in your security strategy. Employees can turn to other unapproved software apps to fill gaps in their workflows, but these software tools often lack proper encryption, multi-factor authentication, or compliance with company security policies.
Worse, IT teams usually don’t even know they exist, so there’s no way to monitor data transfers, user access, or potential vulnerabilities. This creates a perfect entry point for cyberattacks, insider threats, and compliance violations.
Software usage tracking tools expose these risks by finding unauthorized apps and flagging unusual access patterns or user behaviors. IT teams can proactively see which tools employees are using, assess their risk level, and take immediate action. This could mean blocking unsafe apps, integrating secure alternatives, or providing employees with better-approved software solutions themselves.
Improve productivity and employee engagement
Analyzing which features get used most often – and which ones gather dust – can help companies spot workflow bottlenecks and provide additional training. For instance, if data shows that teams spend hours manually entering data into spreadsheets, IT can introduce automation tools or teach shortcuts that save time.
Companies can also adjust their software stack based on real usage data. If analytics show that teams heavily use certain collaboration features in Slack but barely touch similar tools in Microsoft Teams, it makes sense to consolidate to one platform.
Save money with software asset management
Many businesses waste thousands on software licenses that go unused. Employees might be using only a fraction of a tool’s features or entire teams may have paid licenses for access to software they never touch.
Without clear data, businesses continue paying for redundant, outdated, or unnecessary subscriptions. Software usage tracking tools eliminate this waste by showing exactly which tools employees rely on and which ones sit idle. Companies can then reallocate unused licenses, downgrade costly plans, or eliminate unused software altogether—freeing up the budget for more valuable investments.
Use data to drive business strategy
Software usage patterns show actionable insights about how teams actually work and what drives business results. You can analyze which tools employees rely on most heavily and find the core applications that power their most successful projects and teams.
This data helps leaders understand which investments truly matter – for instance, if usage data shows customer service teams solving tickets faster with a specific tool, it’s worth expanding access to improve performance.
Measure ROI and software effectiveness
Usage data provides a clear picture of whether your software investments are actually paying off. Teams can measure concrete metrics like daily active users, time spent on key features, and impact on core business goals. If you invested in a new project management tool, you can track whether it’s reducing meeting time, speeding up project delivery, and being consistently used by teams.
Regular analysis also helps teams refine their tech stack over time. You can compare usage patterns across different tools that serve similar purposes and outline the strongest performers. If data shows one video conferencing platform consistently has better connection quality and higher user satisfaction than alternatives, it makes sense to standardize that solution.
Make data-driven decisions
When you can analyze trends in feature adoption, collaboration patterns, and workflow bottlenecks, it’s easier to spot gaps in current tools and see where new solutions could have the biggest impact. This forward-looking approach transforms software decisions from reactive purchases into strategic investments that solve real business problems.
How To Track Software Usage to Improve Operations
Now that you understand the value of tracking software usage, it’s time to roll up your sleeves and make it happen. We’ll break down the exact steps that separate successful usage tracking initiatives from expensive failures:
Analyze and improve workflows and processes
With software usage tracking, you can map out which features teams use most frequently, so it’s easier to spot repetitive tasks that could be automated or simplified. For example, if you find sales teams manually copying data between their CRM and spreadsheets, you can set up integrations to handle these transfers automatically.
When you see how different teams use the same tools, you often find ways to make everyone’s work easier. Maybe your marketing team discovered a faster way to create reports, but other IT departments don’t know about it. Or perhaps developers found a more efficient project hand-off process that could help the product team too.
Identify areas for improvement
Usage tracking data might show that employees frequently start using a specific feature but quickly abandon it, which suggests they find it confusing or unhelpful. Or you might notice that certain departments barely touch powerful tools they already have, while paying for simpler alternatives.
These insights can help you pinpoint exactly where to focus improvement efforts – whether that means fixing confusing interfaces, adding missing functionalities, or providing better training for existing tools.
Optimize software usage for better productivity
Usage data reveals whether teams fully use key system features or only scratching the surface. If a high-cost tool is used only for basic tasks, you might need more thorough training or a more cost-effective alternative. Likewise, if multiple tools serve the same purpose, consolidating them into a single platform can simplify workflows in your organization.
Software tracking also helps spot where people are working against their tools instead of with them. You might find teams using basic spreadsheets for complex data analysis when you already have specialized tools that could do the job better. These insights let you target improvements where they’ll have the biggest impact on day-to-day work.
How To Analyze Software Usage Data
Understanding software usage starts with tracking the right metrics – not just login counts, but meaningful patterns like which features teams actually use, when they use them, and how long tasks take. With this data, you can spot both quick wins and deeper issues related to usage.
You might also find surprising insights about what drives productivity. Maybe your most successful sales reps use a specific combination of CRM features that others don’t know about. Or maybe certain departments consistently hit roadblocks with software that works fine elsewhere. These patterns help you see what works versus what just looks good on paper.
These analytics provide hard data to support key business decisions rather than relying on gut
feelings or anecdotes. When you can monitor software usage and connect it to business outcomes, you can see which tools drive results. If usage data shows that teams using a particular project management tool complete work 20% faster, that’s concrete evidence for expanding its adoption.
Regular analysis also helps you spot where teams may need extra support to work effectively. When data shows employees repeatedly starting but abandoning certain features, or taking unusually long to complete basic tasks, it signals a need for targeted training.
Instead of generic software workshops, you can focus training resources on specific pain points – like creating quick tutorials for commonly confusing features or setting up mentoring between power users and struggling teams.
Getting Started with Employee Software Usage Tracking
Ready to implement software tracking but not sure where to begin? Skip the expensive mistakes and false starts with this straightforward approach to getting your monitoring program off the ground.
Define Your Software Usage Tracking Strategy
Set clear goals for what you want to learn from software tracking – whether that’s cutting costs, improving employee productivity, or strengthening security. Map out exactly which metrics matter most to your organization, like active usage rates, feature adoption, or time spent in different tools. This helps you avoid collecting mountains of data you’ll never use and instead concentrate on insights that drive real improvements.
Don’t try to figure everything out alone when you can tap into the wealth of resources available from software vendors, industry forums, and professional networks. Most major software providers offer detailed guides, case studies, and support teams to help you implement tracking effectively. Industry groups also often share best practices and templates you can adapt to your needs.
Implement user activity monitoring software
Usage monitoring tools give IT managers a clear window into how employees interact with company software. These tools track specific actions – from basic things like which pages people visit and buttons they click, to more complex patterns of software use, like how they move through multi-step processes.
You can also see which tools new hires pick up quickly, which ones people struggle with, and which ones they stop using after a while. If data shows new employees consistently abandoning a certain tool after a few attempts, that’s a clear signal to look for a more user-friendly alternative or eliminate unnecessary programs.
By tracking long-term application usage patterns, teams can measure true software adoption and spot early warning signs of problems. You can easily identify which departments are getting the most value from different tools, which teams might need extra support, and where licenses are sitting unused.
Create a process to vet and onboard new software
Set up a clear process for evaluating new software requests to prevent wasteful spending. This means checking if existing tools can already handle the need and making sure new purchases don’t overlap with the software you already have. Before approving new tools, require teams to explain exactly how they’ll use them and how many licenses they really need to prevent unnecessary software spend.
Once you decide to buy new software, create a structured onboarding plan. Work with vendors to set up proper training, and identify power users in each team who can help others learn the basics. Break down complex features into simple guides that help employees start using the tool effectively from day one. This thoughtful approach to introducing new software helps ensure people actually use what you’re paying for, instead of letting expensive licenses sit idle while teams stick to their old ways of working.
The post Software Usage Tracking first appeared on Teramind.
Source: itsecuritycentral.teramind.co

