.elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px}
Hidden Employee Monitoring Software
.elementor-widget-text-editor.elementor-drop-cap-view-stacked .elementor-drop-cap{background-color:#69727d;color:#fff}.elementor-widget-text-editor.elementor-drop-cap-view-framed .elementor-drop-cap{color:#69727d;border:3px solid;background-color:transparent}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap{margin-top:8px}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap-letter{width:1em;height:1em}.elementor-widget-text-editor .elementor-drop-cap{float:left;text-align:center;line-height:1;font-size:50px}.elementor-widget-text-editor .elementor-drop-cap-letter{display:inline-block}
Teramind provides hidden employee monitoring, enabling concealed oversight of user activity. Configurable settings allow for comprehensive tracking of system interactions, including applications, websites, and data transfers, without alerting employees. This ensures secure compliance, threat detection, and activity analysis, all while maintaining operational continuity.
.elementor-widget-video .elementor-widget-container{overflow:hidden;transform:translateZ(0)}.elementor-widget-video .elementor-wrapper{aspect-ratio:var(–video-aspect-ratio)}.elementor-widget-video .elementor-wrapper iframe,.elementor-widget-video .elementor-wrapper video{height:100%;width:100%;display:flex;border:none;background-color:#000}@supports not (aspect-ratio:1/1){.elementor-widget-video .elementor-wrapper{position:relative;overflow:hidden;height:0;padding-bottom:calc(100% / var(–video-aspect-ratio))}.elementor-widget-video .elementor-wrapper iframe,.elementor-widget-video .elementor-wrapper video{position:absolute;top:0;right:0;bottom:0;left:0}}.elementor-widget-video .elementor-open-inline .elementor-custom-embed-image-overlay{position:absolute;top:0;right:0;bottom:0;left:0;background-size:cover;background-position:50%}.elementor-widget-video .elementor-custom-embed-image-overlay{cursor:pointer;text-align:center}.elementor-widget-video .elementor-custom-embed-image-overlay:hover .elementor-custom-embed-play i{opacity:1}.elementor-widget-video .elementor-custom-embed-image-overlay img{display:block;width:100%;aspect-ratio:var(–video-aspect-ratio);-o-object-fit:cover;object-fit:cover;-o-object-position:center center;object-position:center center}@supports not (aspect-ratio:1/1){.elementor-widget-video .elementor-custom-embed-image-overlay{position:relative;overflow:hidden;height:0;padding-bottom:calc(100% / var(–video-aspect-ratio))}.elementor-widget-video .elementor-custom-embed-image-overlay img{position:absolute;top:0;right:0;bottom:0;left:0}}.elementor-widget-video .e-hosted-video .elementor-video{-o-object-fit:cover;object-fit:cover}.e-con-inner>.elementor-widget-video,.e-con>.elementor-widget-video{width:var(–container-widget-width);–flex-grow:var(–container-widget-flex-grow)}
.elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block}

The Growing Need for Discrete Employee Monitoring
Unproductive or disengaged employees are only one part of the problem. IT and security teams need to be prepared to handle:
Hybrid and remote work
Supervising employees and ensuring compliance becomes more challenging with remote workers. Discrete monitoring is crucial because it provides visibility into off-site activities without the invasiveness of constant direct oversight, which can erode trust and morale in remote teams.
Accidental insider threats
Even well-intentioned team members can make mistakes that lead to security breaches. Discrete monitoring helps identify risky behavior before it escalates, allowing for proactive intervention without making employees feel constantly suspected.
Productivity drains
Distractions and inefficient workflows impact your team’s productivity. Discrete monitoring allows for data-driven optimization without the Hawthorne effect, where employees artificially change behavior because they know they’re being watched.
Compliance risks
Meeting industry regulations can be complex. Discrete monitoring helps ensure compliance by providing detailed audit logs, which are essential for demonstrating adherence to regulations without disrupting employee workflows.
What Is Stealth Mode?
Stealth mode in Teramind allows the tracking software to operate undetectably on a device, providing discrete monitoring of employee activity. This is achieved through configurable settings that allow you to customize the level of visibility and data collection. Teramind can be hidden from the task manager and system tray, and it runs silently in the background, ensuring employees remain unaware of the monitoring process.
How Organizations Use Teramind’s Hidden Employee Monitoring Tools
Ensure Compliance with Company Policies
.elementor-widget-divider{–divider-border-style:none;–divider-border-width:1px;–divider-color:#0c0d0e;–divider-icon-size:20px;–divider-element-spacing:10px;–divider-pattern-height:24px;–divider-pattern-size:20px;–divider-pattern-url:none;–divider-pattern-repeat:repeat-x}.elementor-widget-divider .elementor-divider{display:flex}.elementor-widget-divider .elementor-divider__text{font-size:15px;line-height:1;max-width:95%}.elementor-widget-divider .elementor-divider__element{margin:0 var(–divider-element-spacing);flex-shrink:0}.elementor-widget-divider .elementor-icon{font-size:var(–divider-icon-size)}.elementor-widget-divider .elementor-divider-separator{display:flex;margin:0;direction:ltr}.elementor-widget-divider–view-line_icon .elementor-divider-separator,.elementor-widget-divider–view-line_text .elementor-divider-separator{align-items:center}.elementor-widget-divider–view-line_icon .elementor-divider-separator:after,.elementor-widget-divider–view-line_icon .elementor-divider-separator:before,.elementor-widget-divider–view-line_text .elementor-divider-separator:after,.elementor-widget-divider–view-line_text .elementor-divider-separator:before{display:block;content:””;border-block-end:0;flex-grow:1;border-block-start:var(–divider-border-width) var(–divider-border-style) var(–divider-color)}.elementor-widget-divider–element-align-left .elementor-divider .elementor-divider-separator>.elementor-divider__svg:first-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-left .elementor-divider-separator:before{content:none}.elementor-widget-divider–element-align-left .elementor-divider__element{margin-left:0}.elementor-widget-divider–element-align-right .elementor-divider .elementor-divider-separator>.elementor-divider__svg:last-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-right .elementor-divider-separator:after{content:none}.elementor-widget-divider–element-align-right .elementor-divider__element{margin-right:0}.elementor-widget-divider–element-align-start .elementor-divider .elementor-divider-separator>.elementor-divider__svg:first-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-start .elementor-divider-separator:before{content:none}.elementor-widget-divider–element-align-start .elementor-divider__element{margin-inline-start:0}.elementor-widget-divider–element-align-end .elementor-divider .elementor-divider-separator>.elementor-divider__svg:last-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-end .elementor-divider-separator:after{content:none}.elementor-widget-divider–element-align-end .elementor-divider__element{margin-inline-end:0}.elementor-widget-divider:not(.elementor-widget-divider–view-line_text):not(.elementor-widget-divider–view-line_icon) .elementor-divider-separator{border-block-start:var(–divider-border-width) var(–divider-border-style) var(–divider-color)}.elementor-widget-divider–separator-type-pattern{–divider-border-style:none}.elementor-widget-divider–separator-type-pattern.elementor-widget-divider–view-line .elementor-divider-separator,.elementor-widget-divider–separator-type-pattern:not(.elementor-widget-divider–view-line) .elementor-divider-separator:after,.elementor-widget-divider–separator-type-pattern:not(.elementor-widget-divider–view-line) .elementor-divider-separator:before,.elementor-widget-divider–separator-type-pattern:not([class*=elementor-widget-divider–view]) .elementor-divider-separator{width:100%;min-height:var(–divider-pattern-height);-webkit-mask-size:var(–divider-pattern-size) 100%;mask-size:var(–divider-pattern-size) 100%;-webkit-mask-repeat:var(–divider-pattern-repeat);mask-repeat:var(–divider-pattern-repeat);background-color:var(–divider-color);-webkit-mask-image:var(–divider-pattern-url);mask-image:var(–divider-pattern-url)}.elementor-widget-divider–no-spacing{–divider-pattern-size:auto}.elementor-widget-divider–bg-round{–divider-pattern-repeat:round}.rtl .elementor-widget-divider .elementor-divider__text{direction:rtl}.e-con-inner>.elementor-widget-divider,.e-con>.elementor-widget-divider{width:var(–container-widget-width,100%);–flex-grow:var(–container-widget-flex-grow)}
Track employee computer activity discretely to verify adherence to company policies, including internet usage, app usage, and data handling.
Detect and Prevent Insider Threats
Identify potentially harmful activities like unauthorized data access, suspicious email communication, and attempts to bypass security protocols.
Enhance Productivity Management
Gain insights into employee activity patterns and identify areas for improvement, optimizing workflows and addressing unproductive behaviors.
Mitigate Risks and Liabilities
Maintain detailed records of employee activity, including activity logs, video recordings, and keystroke logs, which can be crucial in legal or compliance situations.
Improve Workforce Visibility
Effectively monitor remote employee activity without disrupting their workflow. Ensure productivity, adherence to company policies, and appropriate use of company resources.
Protect Sensitive Data
Prevent data breaches by monitoring for suspicious file transfers, unauthorized access to confidential information, and other potentially harmful activities.
Top Features of Teramind’s Hidden Employee Monitoring
Undetectable Employee Monitoring
Teramind operates silently and invisibly, ensuring employees remain unaware of its presence.
- Operates with stealth deployment options that run invisibly in the background
- Features tamper-proof installation that prevents detection or removal by standard users
- Utilizes minimal system resources to avoid performance impacts that might alert employees
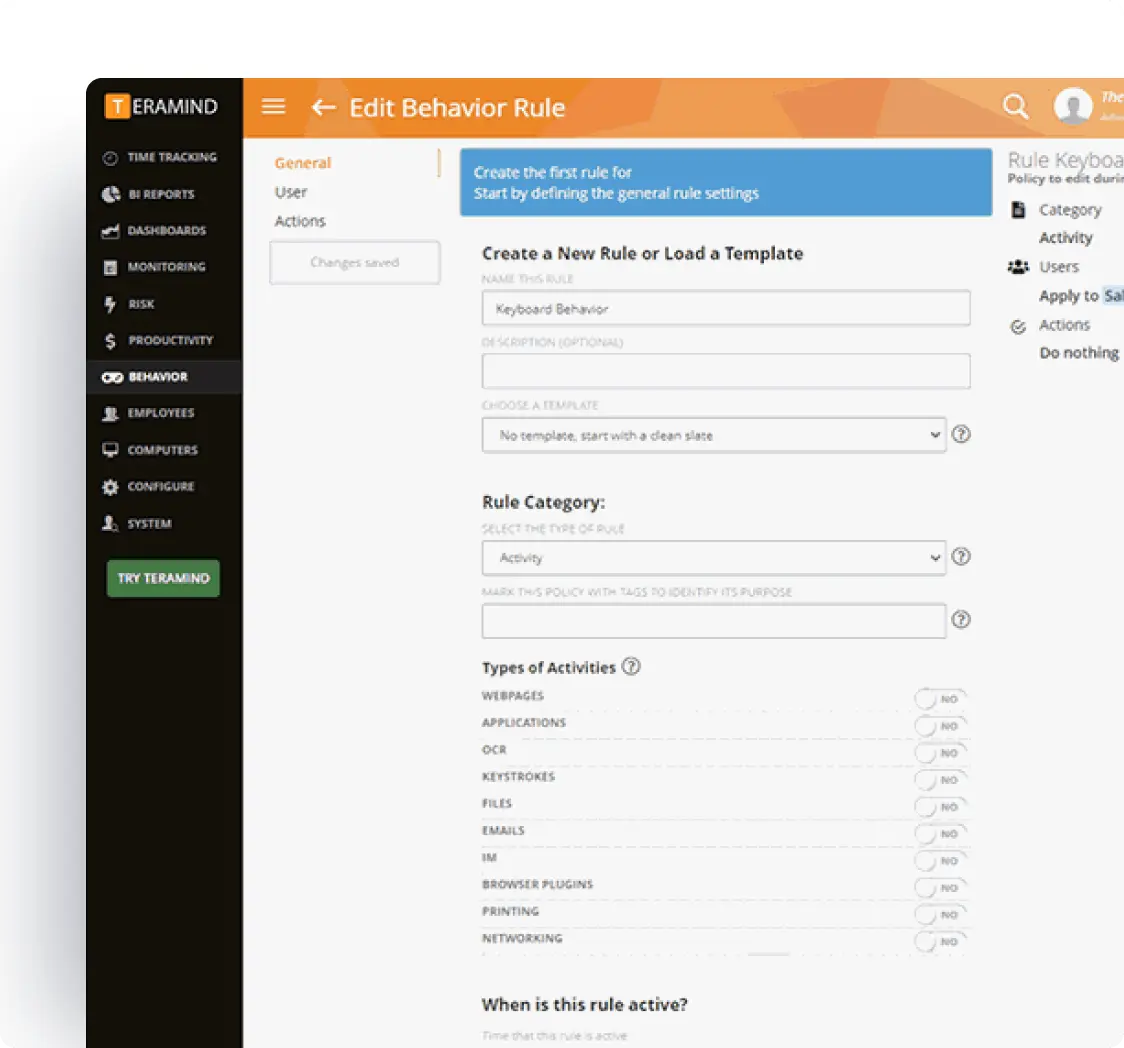
Highly Customizable Settings
Configure monitoring parameters to meet specific needs, including data collection levels, visibility options, and alert triggers.
- Offers granular policy configuration for different departments, teams, or individual roles
- Provides flexible scheduling options to enable monitoring during specific time periods only
- Includes customizable alert thresholds that adapt to your organization’s unique risk profile
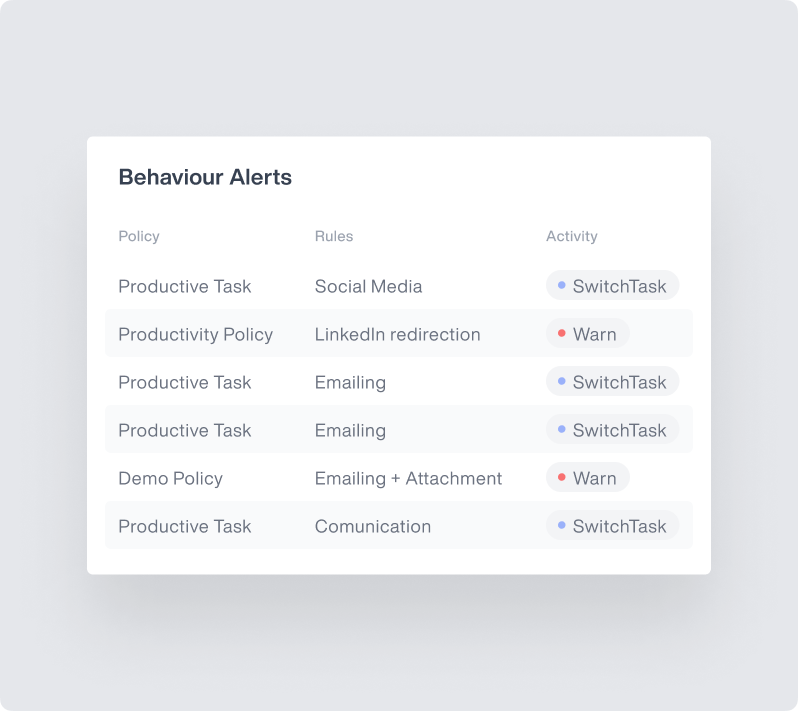
Advanced User Behavior Analytics
Automatically detect anomalies and suspicious activities based on predefined rules and behavioral baselines.
- Employs machine learning to establish normal behavior patterns for each employee
- Identifies deviations from typical work patterns to flag potential insider threats
- Creates risk scores based on cumulative suspicious activities for prioritized investigation
Real-Time Screen Monitoring
View live feeds of employee screens for direct observation and immediate response to potential issues.
- Delivers high-definition screen recordings with minimal latency for immediate oversight
- Enables session recording playback with DVR-like controls for thorough review
- Includes screenshot capture at configurable intervals or triggered by specific actions
Comprehensive Data Collection
Generate comprehensive activity reports and analyze data to identify trends, assess employee productivity, and ensure compliance.
- Records keystrokes and text input across all applications and websites
- Tracks file operations including creation, modification, deletion, and transfer attempts
- Monitors clipboard activity to detect sensitive data being copied between applications
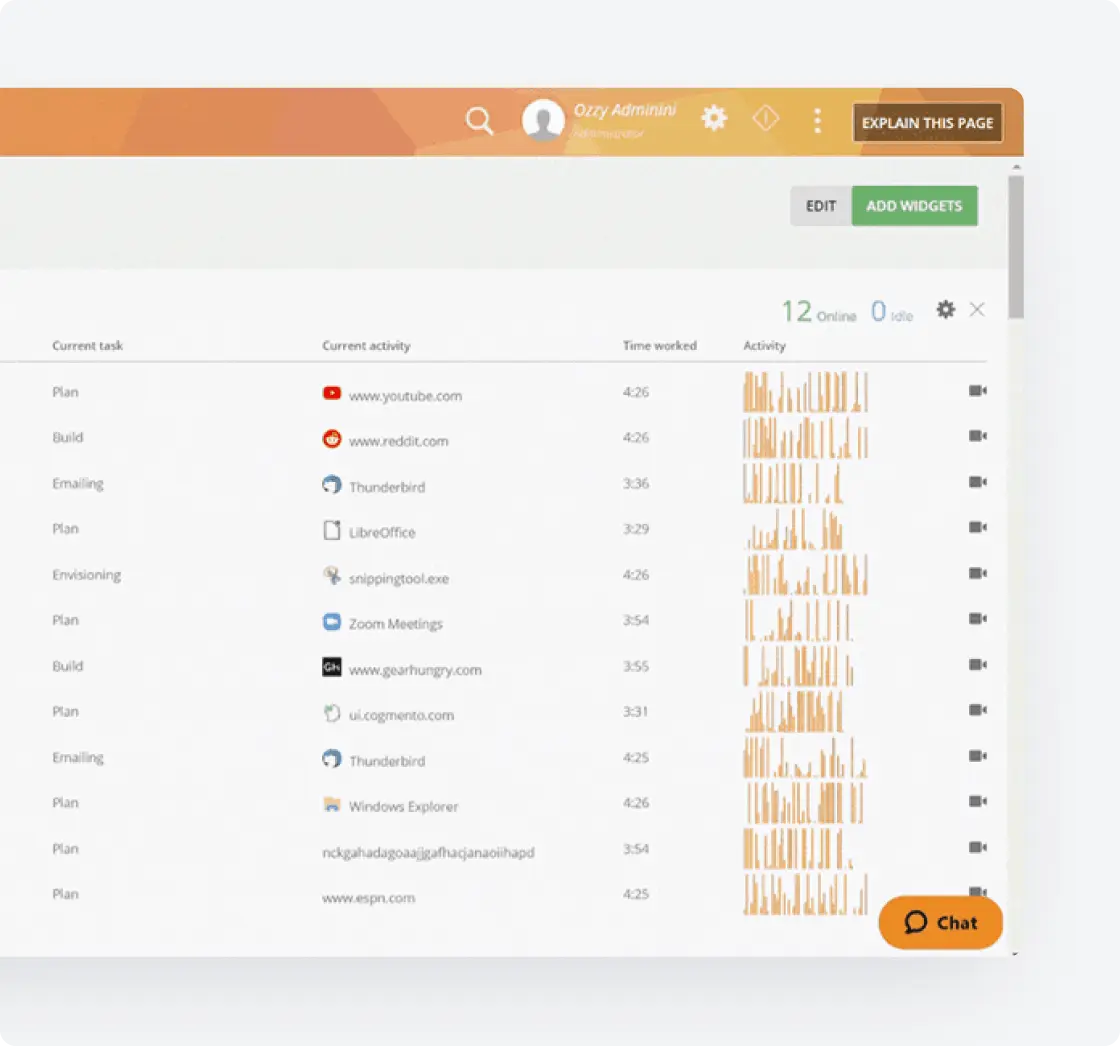
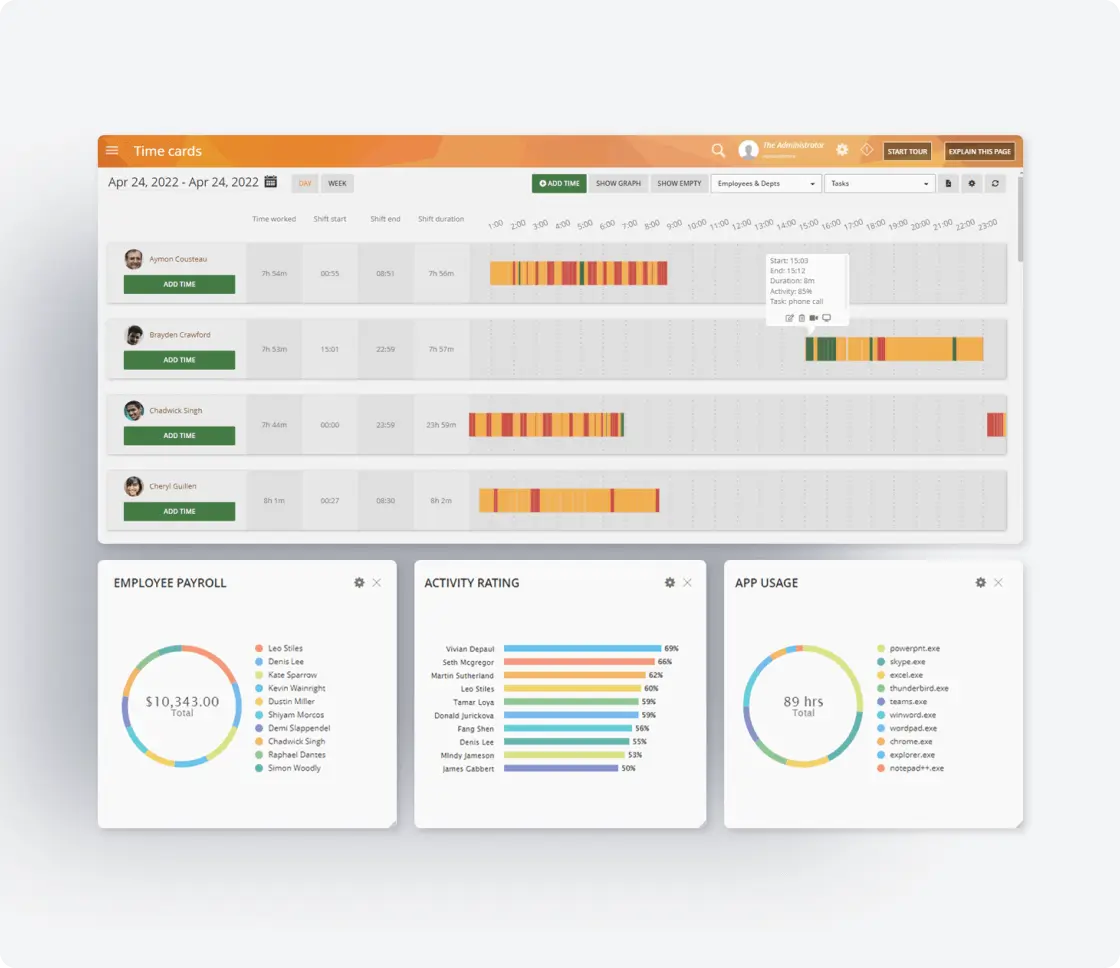
Detailed Reporting and Analytics
Generate comprehensive activity reports and analyze data to identify trends, assess employee productivity, and ensure compliance.
- Presents visual dashboards with key metrics for at-a-glance productivity assessment
- Generates customizable reports that can be scheduled and automatically distributed
- Offers exportable audit logs for compliance documentation and incident investigation
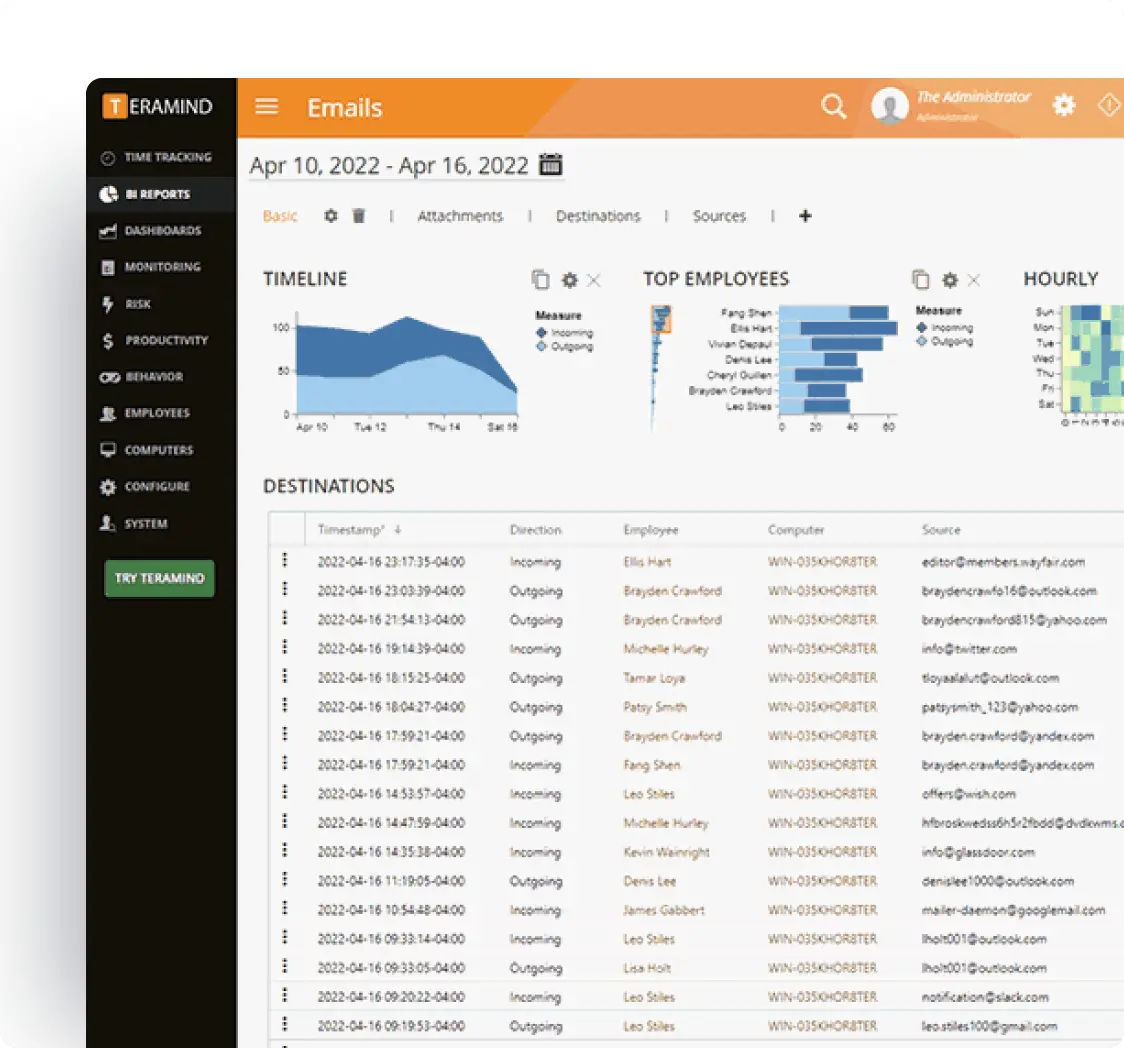
How Teramind Stacks Up
See why Teramind is the best employee monitoring software on the market right now.
Teramind
ActivTrak
Currentware
Monitask
Monitoring Scope
Applications, websites, emails, files, social media, IMs, keystrokes, screen activity
User behavior, applications, websites
Internet usage, applications, device control
Time tracking, applications, websites, screenshots
Stealth Mode
Hidden from task manager, runs silently, customizable
Limited stealth capabilities
Limited to BrowseReporter module
Basic stealth version
Real-time Monitoring
Screen monitoring and alerts with playback
Activity-based alerts
Limited real-time capabilities
Basic real-time activity tracking
User & Entity Behavior Analytics (UEBA)
AI-powered anomaly detection
Basic activity alarms
No dedicated UEBA features
No dedicated UEBA features
Productivity Analysis
Detailed reports, real-time insights, customizable metrics
Productivity tracking and reporting
Basic activity tracking in BrowseReporter
Limited time tracking, productivity reports
Remote Workforce Monitoring
Robust features, location monitoring
Location-specific insights
No dedicated remote features
Suitable for remote teams
Security & Compliance
Keystroke logging, email monitoring, audit trails, customizable policies, real-time enforcement
Basic activity alarms for compliance risks
Internet filtering, device control
Limited IP and VPN tracking
Teramind’s Core Features for Employee Monitoring
Leverage Teramind’s unparalleled power to solve your workforce challenges.
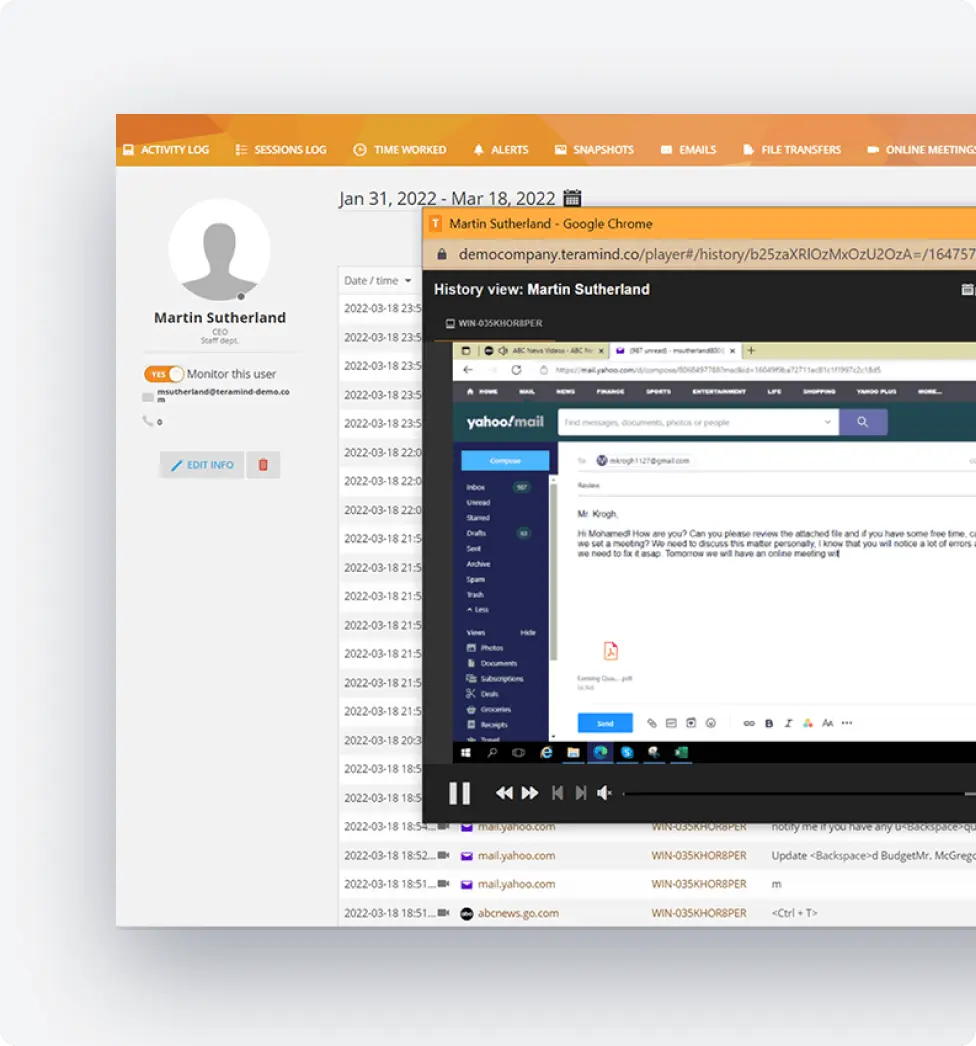
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
.elementor-widget-image-box .elementor-image-box-content{width:100%}@media (min-width:768px){.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper,.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{display:flex}.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{text-align:end;flex-direction:row-reverse}.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper{text-align:start;flex-direction:row}.elementor-widget-image-box.elementor-position-top .elementor-image-box-img{margin:auto}.elementor-widget-image-box.elementor-vertical-align-top .elementor-image-box-wrapper{align-items:flex-start}.elementor-widget-image-box.elementor-vertical-align-middle .elementor-image-box-wrapper{align-items:center}.elementor-widget-image-box.elementor-vertical-align-bottom .elementor-image-box-wrapper{align-items:flex-end}}@media (max-width:767px){.elementor-widget-image-box .elementor-image-box-img{margin-left:auto!important;margin-right:auto!important;margin-bottom:15px}}.elementor-widget-image-box .elementor-image-box-img{display:inline-block}.elementor-widget-image-box .elementor-image-box-title a{color:inherit}.elementor-widget-image-box .elementor-image-box-wrapper{text-align:center}.elementor-widget-image-box .elementor-image-box-description{margin:0}
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
Is hidden tracking of employee computers and other devices legal?
Yes, hidden tracking of employee computers and devices can be legal, but it depends on several factors, including your location, the specific monitoring features used, and how the monitoring is implemented. Generally, employers have the right to monitor their employees’ computer usage on company-owned devices.
However, it’s crucial to:
-
Inform employees: Be transparent with employees about the monitoring activities, even if the monitoring system itself is hidden.
-
Obtain consent: In some jurisdictions, obtaining employee consent for monitoring is required.
-
Respect employee privacy: Avoid monitoring personal devices or activities outside of work time.
-
Comply with regulations: Adhere to all relevant laws and regulations regarding employee monitoring, such as data protection and privacy laws.
It’s recommended to consult with legal counsel to ensure your employee monitoring solution complies with all applicable laws and regulations.
What is a stealth software tracker?
A stealth software tracker, also known as hidden employee tracking software or computer monitoring software, is a type of monitoring system that operates undetectably on a device. It tracks employee activity without their knowledge, capturing data such as websites visited, apps used, emails sent, and keystrokes typed.
Why do employers ask for stealth mode?
Employers may choose to use stealth mode in their employee monitoring solution for several reasons:
-
Accurate data collection: Stealth mode allows for the collection of unbiased data on employee workday and general activity, as employees are less likely to alter their behavior when they are unaware of the monitoring. This provides more accurate insights into employee performance and work time allocation.
-
Prevent insider threats: Stealth mode can help identify potentially harmful activities like unauthorized access to sensitive information or suspicious email communication, which employees might attempt to hide if they knew they were being monitored.
-
Maintain trust: While transparency is important, visible monitoring can sometimes create a sense of distrust and negatively impact employee engagement. Stealth mode allows for productivity monitoring while maintaining a sense of normality in the work environment.
-
Address specific concerns: Employers might use stealth mode to address specific concerns, such as suspected employee time theft, policy violations, or data security breaches, without alerting the employees in question.
The post Hidden Employee Monitoring Software first appeared on Teramind.
Source: itsecuritycentral.teramind.co

