FISMA Compliance Monitoring: Real-Time Employee Activity Tracking for Federal Agencies
Monitor user behavior, prevent data breaches, and ensure FISMA compliance with Teramind’s employee monitoring platform that tracks, records, and analyzes all activities across federal information systems.

Why Choose Teramind for FISMA Compliance
Teramind provides federal agencies and contractors with powerful tools to achieve FISMA compliance, protect sensitive data, and prevent security incidents through automated security controls and continuous monitoring processes.
Continuous Monitoring
Meet the Federal Information Security Management Act’s mandatory continuous monitoring requirements with real-time tracking of user activities, system configurations, and security controls across your organization’s federal information systems.
Comprehensive Reporting
Generate detailed security reports with crucial data for required annual security reviews and FISMA compliance status reporting, helping federal agencies demonstrate adherence to security requirements while saving time and resources.
Insider Threat Prevention
Protect against data breaches with advanced behavioral analytics that identify suspicious activities and policy violations before they compromise sensitive government information or lead to security incidents.
Key Teramind Features for FISMA Compliance
Teramind offers a comprehensive suite of tools specifically designed to help government agencies and contractors achieve and maintain FISMA compliance while protecting federal information systems.
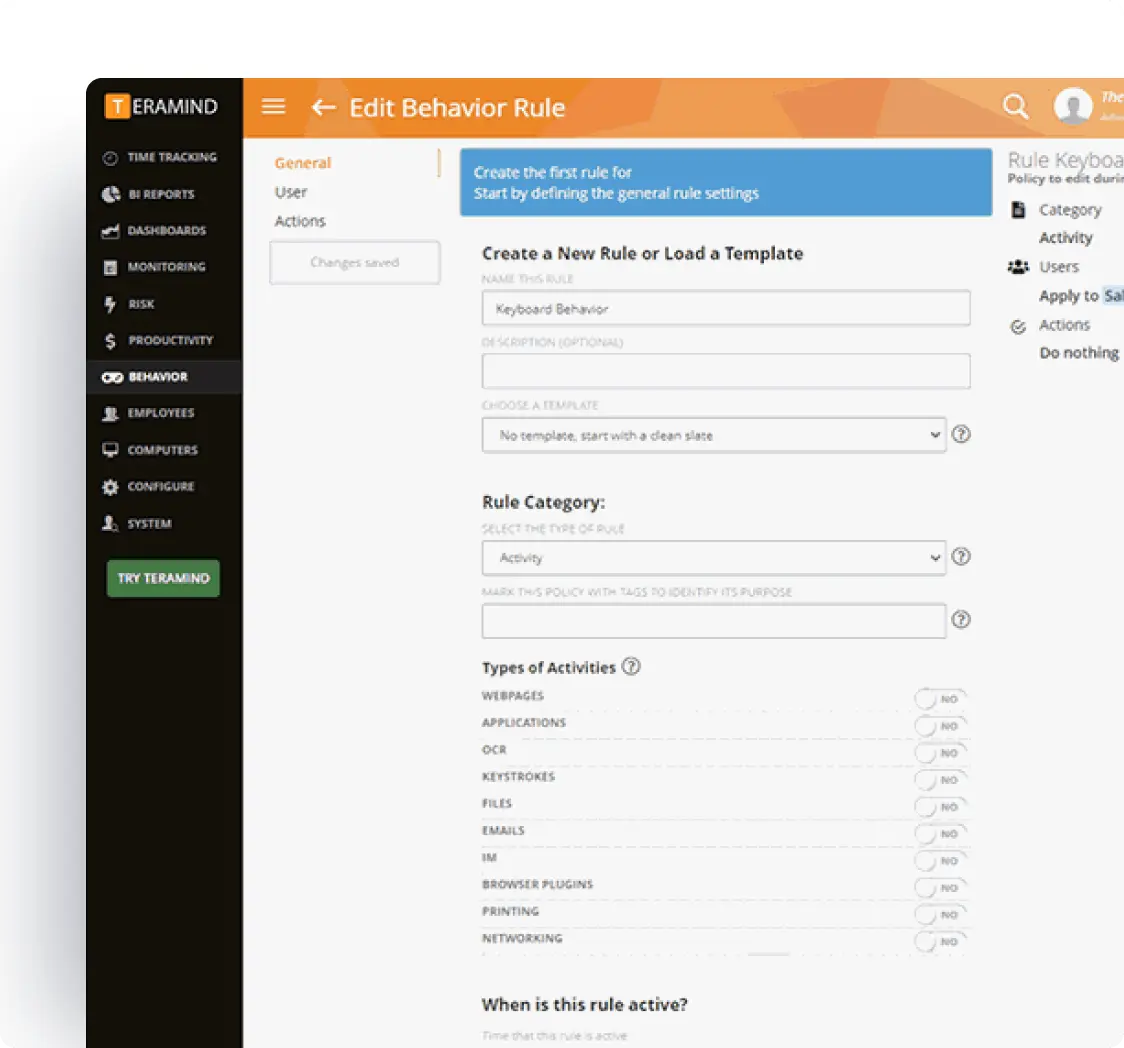
Risk Assessment & Categorization
Identify and classify information systems according to FISMA’s risk-based approach to security.
- Sophisticated risk algorithm identifies high-risk users and system components
- Categorize sensitive data based on potential impact levels
- Track risk metrics through customizable dashboards
- Generate comprehensive risk assessments for compliance documentation
Access Control Management
Implement and enforce the principle of least privilege across all federal information systems and users.
- Identity-based authentication for secure system access
- Segregated access control for viewing and editing sensitive information
- Privileged user monitoring with additional scrutiny
- Role-based permissions aligned with security controls requirements
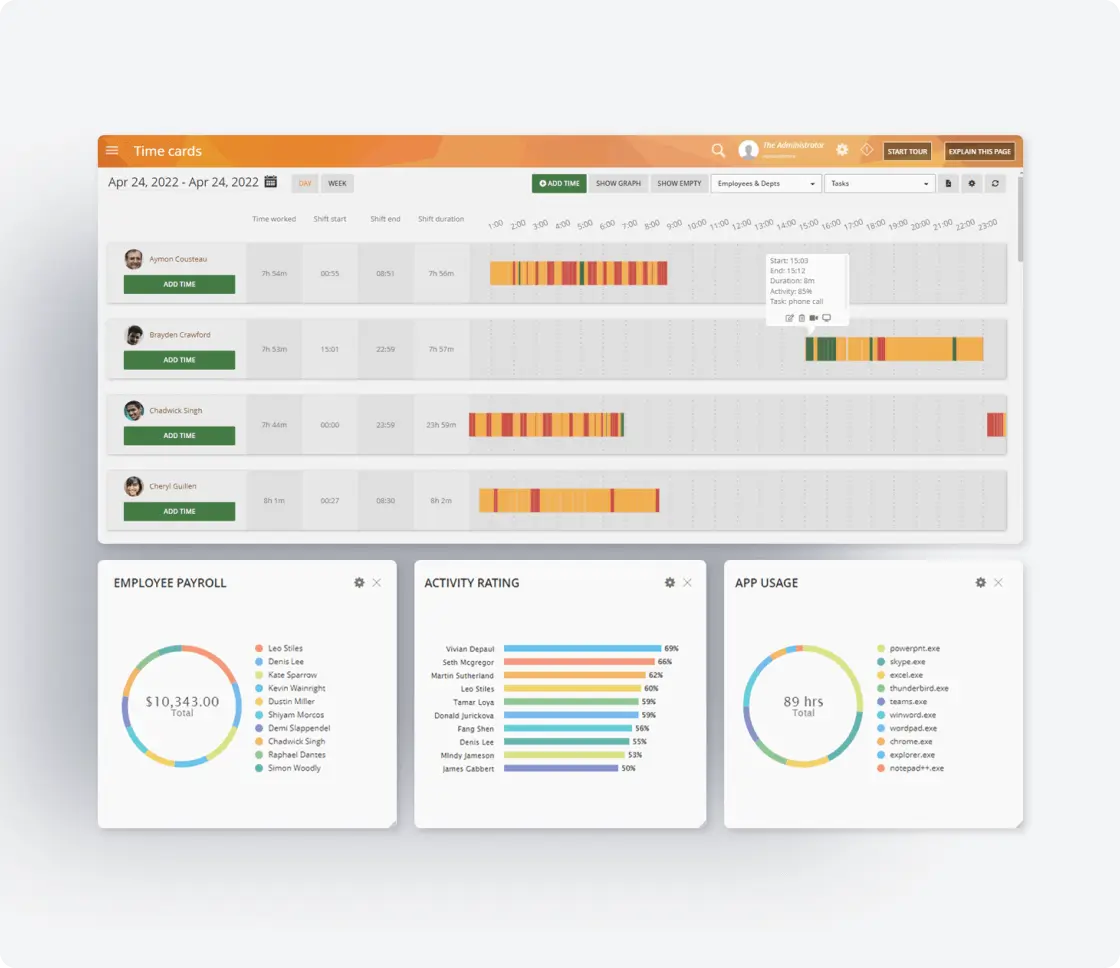
Continuous Endpoint Monitoring
Meet FISMA’s continuous monitoring mandate with real-time surveillance of all endpoint activities.
- 24/7 real-time visual screen recording of user activities on federal information systems
- Hidden agent tracks all activity customized to your monitoring needs
- Automatic detection of system configuration changes
- Monitoring of all data transfers and access attempts
- Alerts for suspicious or unauthorized activities that could lead to data breaches
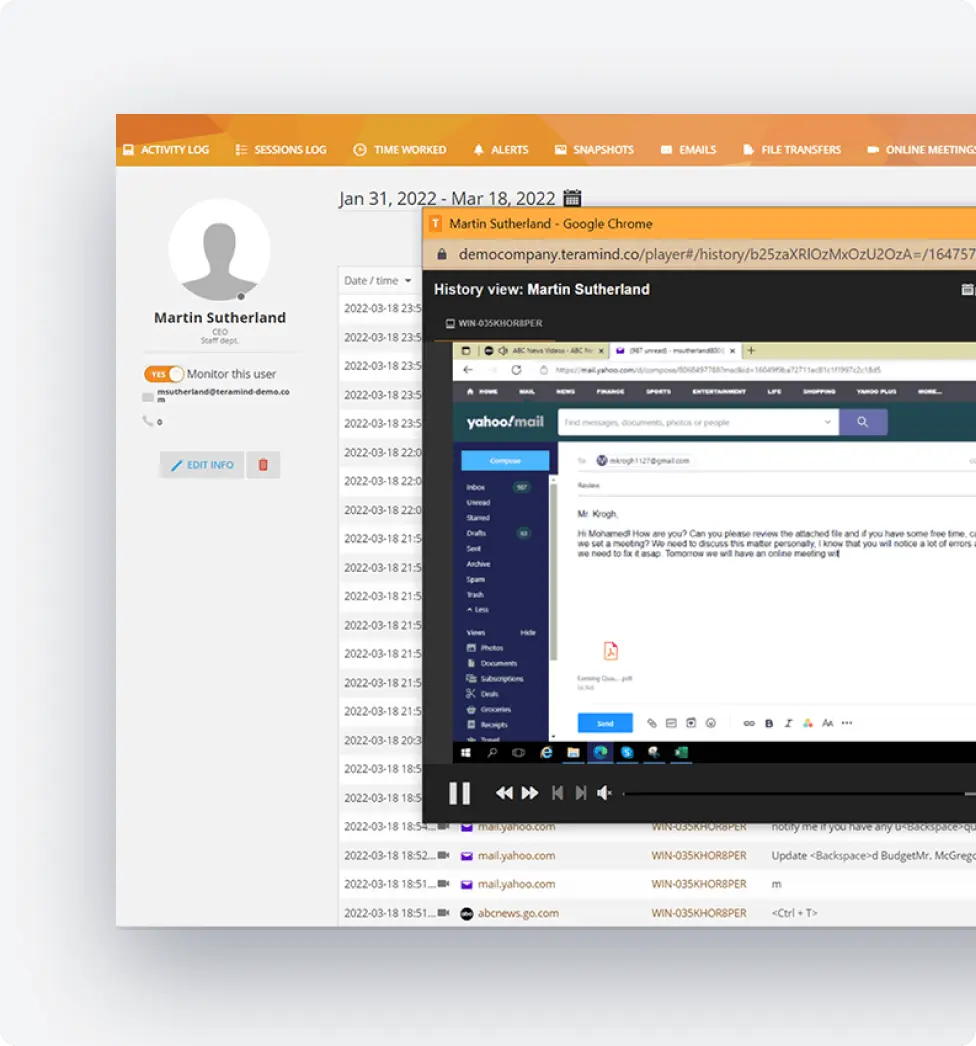
Comprehensive Audit Trails
Maintain detailed records of all system access to demonstrate compliance during annual security reviews.
- Create immutable activity logs for regulatory submissions
- Provide detailed user activity timelines for security incidents investigation
- Offer session recordings with playback for complete context of events
- Maintain audit trails across all endpoints, including remote workstations
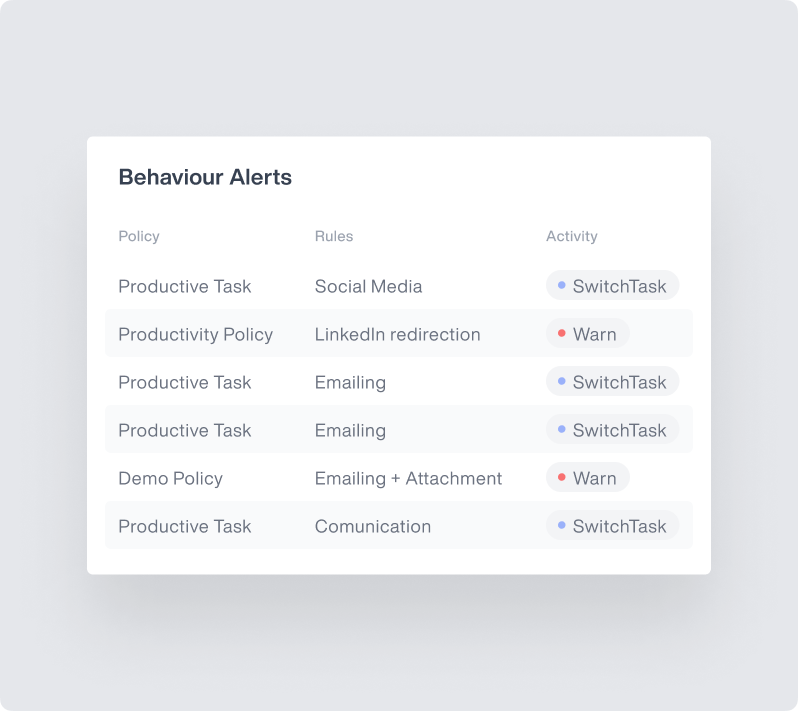
Automated Incident Response
Quickly identify and remediate potential security incidents with powerful response tools.
- Automated blocking of unauthorized activities
- Customizable compliance playbooks for different security scenarios
- Immediate alerts to security personnel
- Detailed forensic evidence collection for security incidents analysis
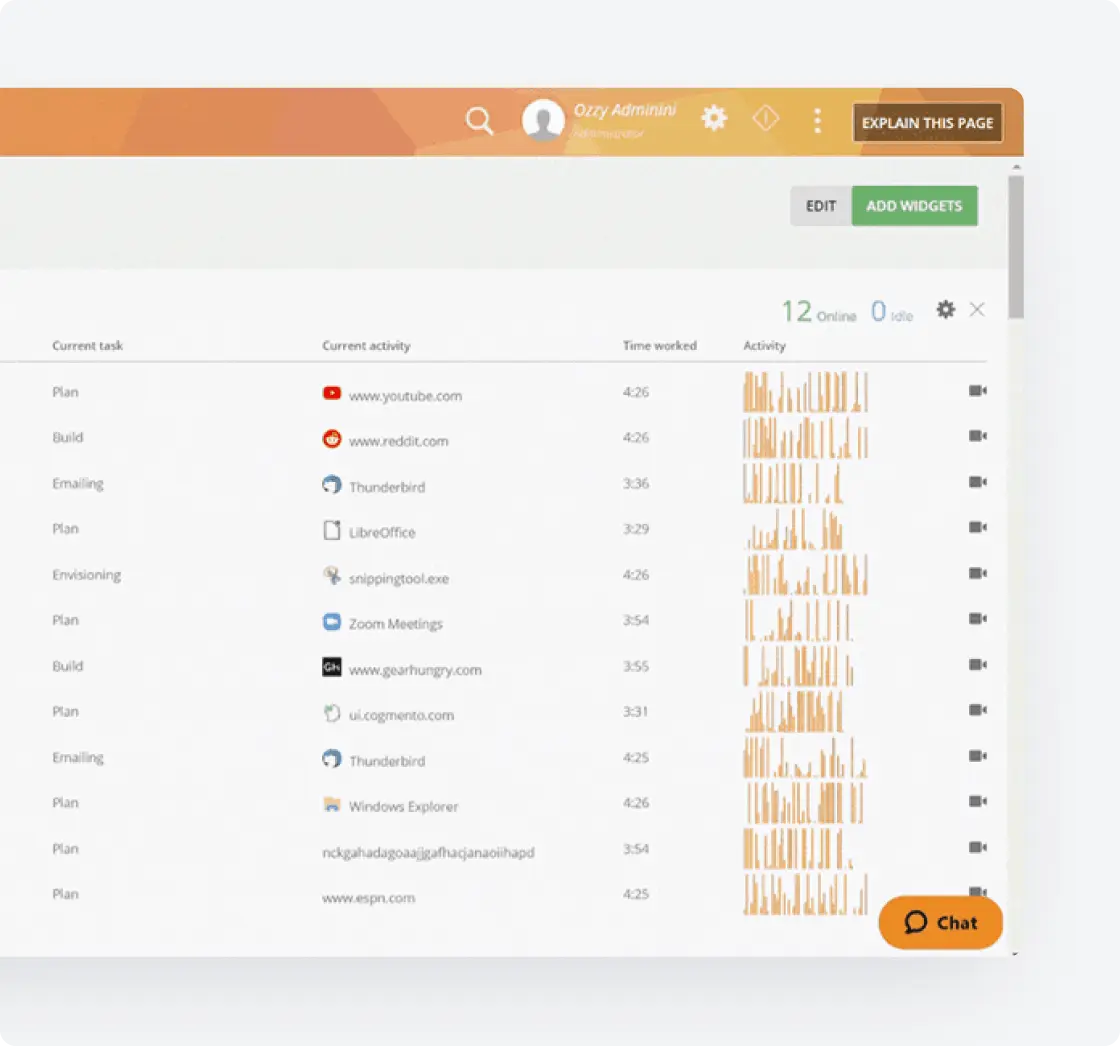
Third-Party Vendor Management
Monitor and control third-party access to federal information systems and sensitive data.
- Track activities of contractors accessing government information
- Enforce security controls for all users regardless of origin
- Verify user authenticity to prevent unauthorized access
- Monitor compliance with federal security requirements for all contractors
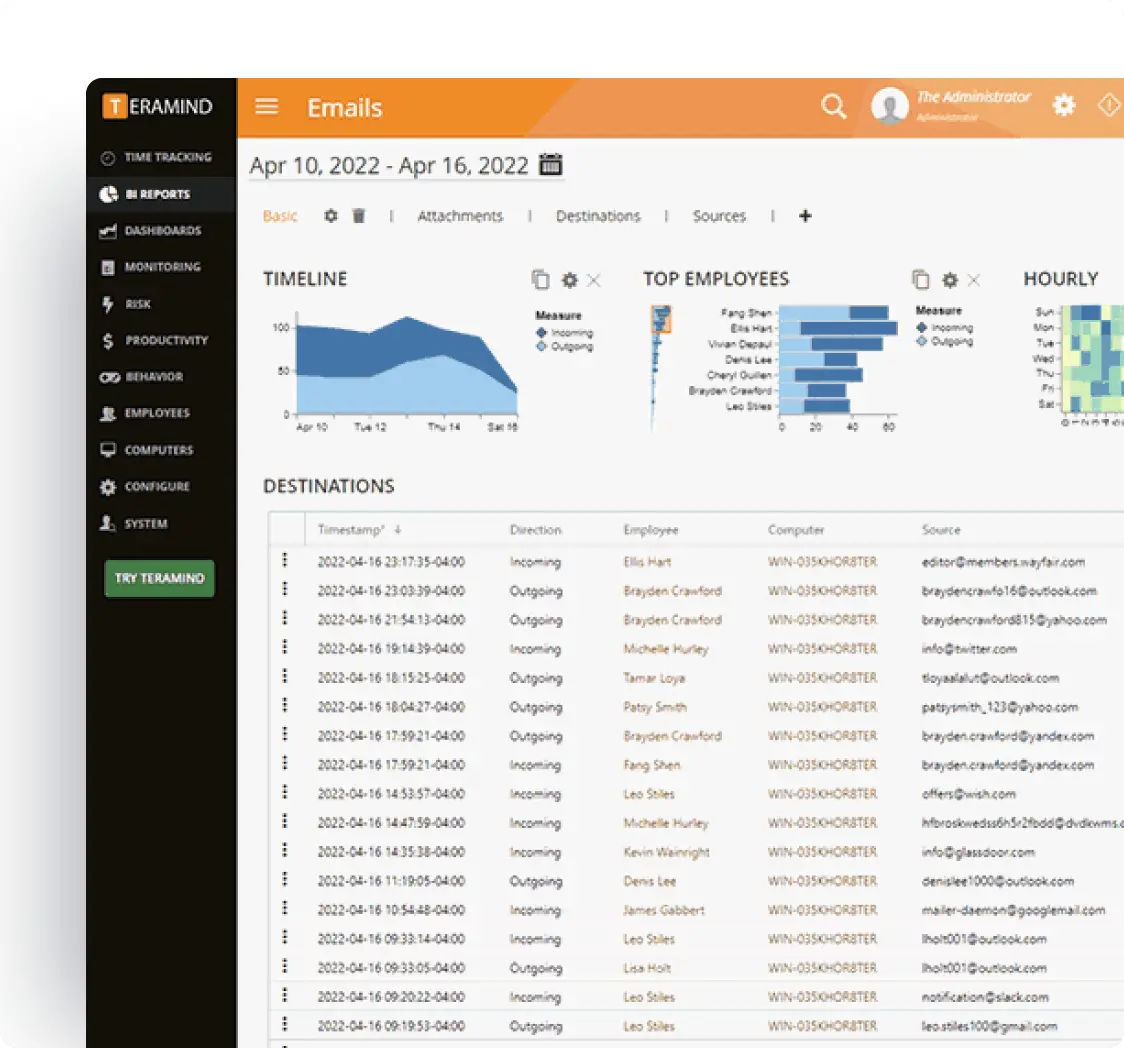
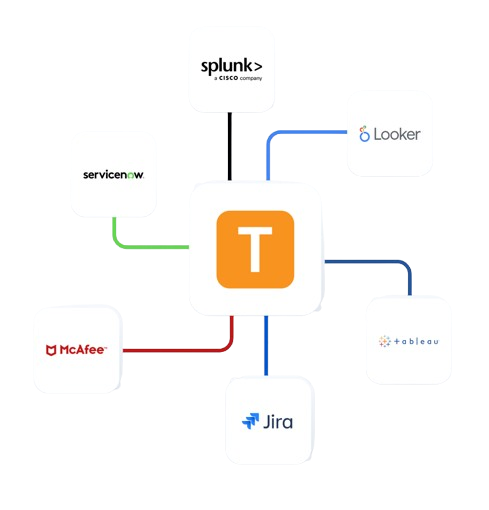
Enterprise Integrations
Integrate Teramind with your existing security infrastructure to enhance FISMA compliance monitoring.
- Integrate with leading SIEM solutions like Splunk, ArcSight, and QRadar to centralize security event monitoring
- Connect with SOAR platforms to automate incident response for potential data privacy violations
- Leverage Common Event Format (CEF) for standardized security event reporting
- Enhance existing security tools with Teramind’s detailed user behavior analytics
Teramind’s Core Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“The interface and reporting capabilities of Teramind remain unmatched compared to other products we have tried. Overall, Teramind is far more advanced than other competitors. They are definitely raising the bar and I’ll back them up any day.”
Ricky H.
Government Administration
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Rene H.
Head IT Security
“This software has allowed us to save from a potential data breach and being able to catch people leaving who tried to take our IP. Very good software. A bit on the expensive side but worth every penny. Functionality is easy to get around. Has a great GUI.”
Milena L.
IT Manager
FAQs
What are the five FISMA pillars?
While FISMA doesn’t specifically outline just five rules, it establishes five core pillars that define compliance requirements: categorizing information systems based on risk, implementing appropriate security controls, conducting regular risk assessments, creating and maintaining a comprehensive system security plan, and establishing continuous monitoring processes. These fundamental elements form the backbone of the Federal Information Security Management Act framework, requiring government agencies to protect sensitive data through structured information security programs that integrate both technical and administrative safeguards while maintaining proper documentation of all security measures implemented across federal information systems.
What does it mean to be FISMA compliant?
Being FISMA compliant means an organization has implemented all necessary security controls to protect federal information systems and conducts annual security reviews to verify these protections remain effective. Compliance requires federal agencies to maintain an inventory of IT systems, categorize information based on risk, develop system security plans, implement appropriate security controls, conduct regular risk assessments, and establish continuous monitoring capabilities. Teramind’s FISMA compliance monitoring solution helps organizations achieve and maintain these requirements by providing real-time user activity monitoring, automated security enforcement, comprehensive audit trails, and detailed reporting capabilities that demonstrate adherence to the Federal Information Security Management Act’s security standards.
Who complies with FISMA?
FISMA compliance requirements apply primarily to federal agencies within the executive branch of the U.S. government, but extend to contractors, service providers, and other organizations that process or store sensitive data on behalf of federal information systems. Any organization that supports government agencies must implement the same level of information security protocols and continuous monitoring practices to protect government information. Teramind helps both government agencies and their partners maintain FISMA compliance through comprehensive security controls monitoring, automated risk assessments, and detailed audit trails that document all user activities, system changes, and security incidents across federal information systems.
What is FISMA vs NIST?
FISMA (Federal Information Security Management Act) is the legislation that mandates cybersecurity requirements for federal agencies, while NIST (National Institute of Standards and Technology) provides the specific guidelines and security controls needed to achieve FISMA compliance. NIST develops the standards, frameworks, and security control requirements that organizations use to implement FISMA, particularly through Special Publication 800-53 which details security control specifications. Teramind’s comprehensive monitoring solution aligns with both FISMA requirements and NIST guidelines by providing the continuous monitoring capabilities, security control enforcement, and detailed audit trails necessary for federal agencies to protect sensitive data, prevent data breaches, and document compliance with federal information security requirements.
The post FISMA Compliance Monitoring first appeared on Teramind.
Source: itsecuritycentral.teramind.co

