.elementor-heading-title{padding:0;margin:0;line-height:1}.elementor-widget-heading .elementor-heading-title[class*=elementor-size-]>a{color:inherit;font-size:inherit;line-height:inherit}.elementor-widget-heading .elementor-heading-title.elementor-size-small{font-size:15px}.elementor-widget-heading .elementor-heading-title.elementor-size-medium{font-size:19px}.elementor-widget-heading .elementor-heading-title.elementor-size-large{font-size:29px}.elementor-widget-heading .elementor-heading-title.elementor-size-xl{font-size:39px}.elementor-widget-heading .elementor-heading-title.elementor-size-xxl{font-size:59px}
Employee Email Monitoring Software
From Click to Send: No Email Action Goes Unnoticed
.elementor-widget-text-editor.elementor-drop-cap-view-stacked .elementor-drop-cap{background-color:#69727d;color:#fff}.elementor-widget-text-editor.elementor-drop-cap-view-framed .elementor-drop-cap{color:#69727d;border:3px solid;background-color:transparent}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap{margin-top:8px}.elementor-widget-text-editor:not(.elementor-drop-cap-view-default) .elementor-drop-cap-letter{width:1em;height:1em}.elementor-widget-text-editor .elementor-drop-cap{float:left;text-align:center;line-height:1;font-size:50px}.elementor-widget-text-editor .elementor-drop-cap-letter{display:inline-block}
Cut incident response time in half and reduce false security alarms by 85% with intelligent monitoring that knows the difference.
.elementor-widget-image{text-align:center}.elementor-widget-image a{display:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:middle;display:inline-block}


91% of Cyber Attacks Start with Email. The Average Data Breach Costs $4.88 Million.
All it takes is one wrong email—whether accidental or intentional—to put your company at risk.
- 258 days: The average time taken to identify and contain a data breach.
- 71%: Percentage of organizations that experienced at least one successful phishing attack.
- 6 in 10: Number of small businesses that suffer a cyberattack and go out of business within six months.
See Beyond The Inbox
Without visibility into workplace email activity, you’re leaving the door wide open to insider threats, data leaks, and compliance failures.
Stay Ahead Of Threats with Real-Time Email Monitoring
Track every inbound and outbound email with instant alerts for unauthorized sharing, suspicious attachments, and abnormal activity.

Block Leaks Before They Happen
Automatically detect and prevent sensitive information from being shared externally through emails, attachments, or BCC misuse.
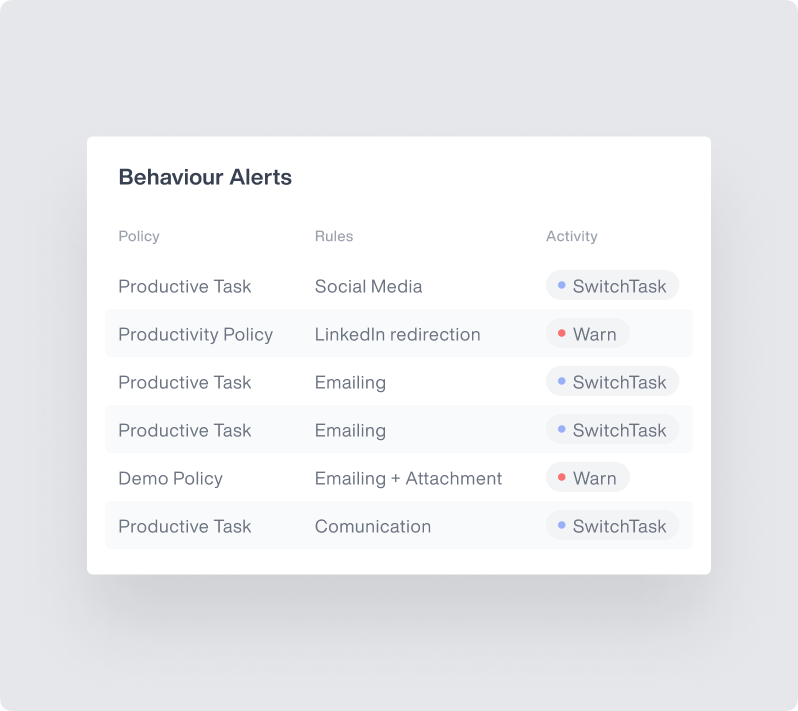
Catch Suspicious Activity Instantly With Insider Threat Detection
Detect mass email forwarding, excessive external communication, and unauthorized data exfiltration in real-time.
Stay Compliant with Regulations
Maintain detailed email logs and audit trails to ensure compliance with HIPAA, GDPR, SOC2, and other industry standards.
Prevent Unapproved File Sharing
Monitor file attachments in emails to stop unauthorized file transfers that could lead to intellectual property theft.
Control What Leaves Your Network
Set up custom keyword alerts to flag sensitive phrases and prevent confidential data from leaving your organization.
Core Teramind Features
Leverage Teramind’s unparalleled power to solve your workforce challenges.
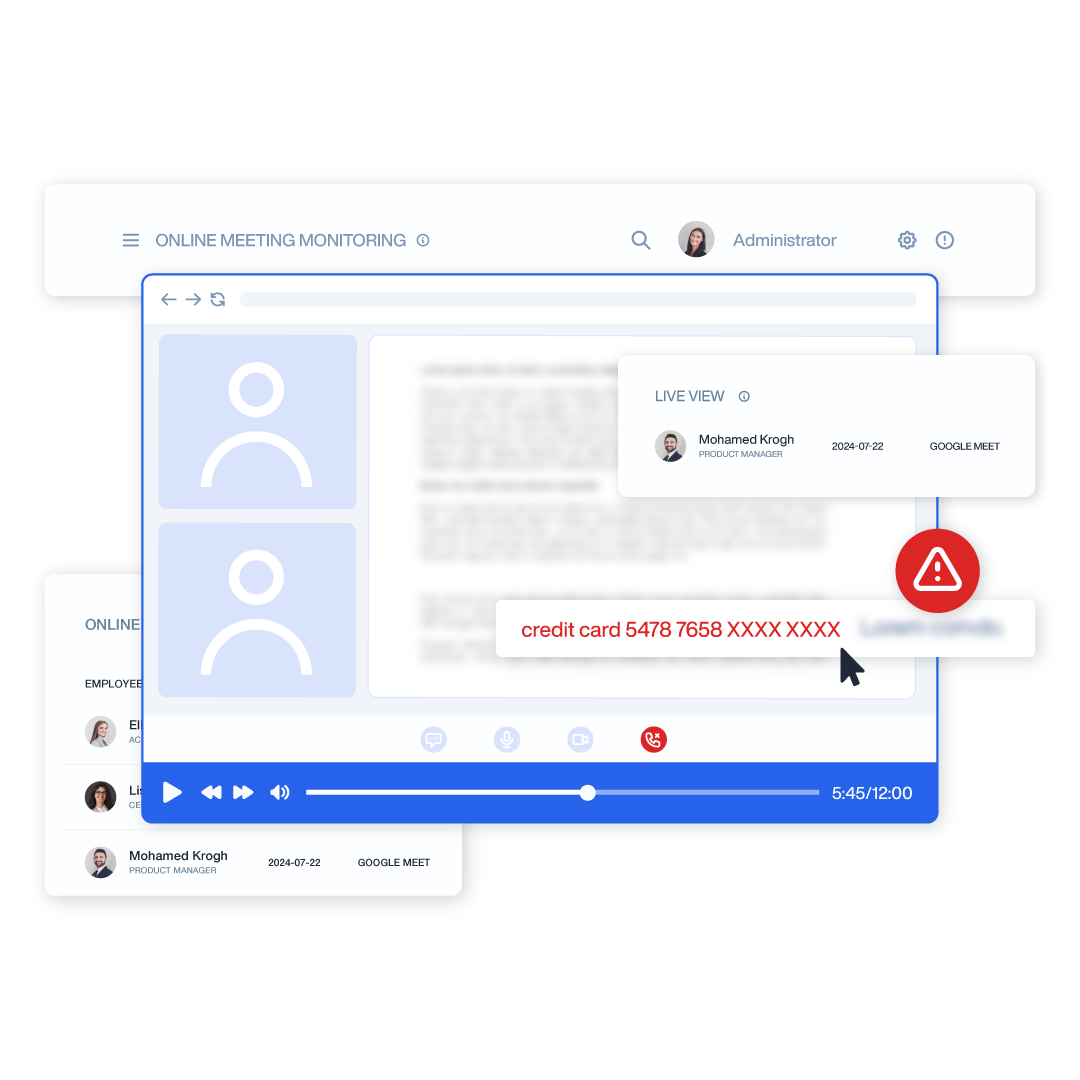
Live View & Historical Playback
Monitor employee screens in real-time or review past activity with historical playback to gain complete visibility into user activity and computer activity.
.elementor-widget-divider{–divider-border-style:none;–divider-border-width:1px;–divider-color:#0c0d0e;–divider-icon-size:20px;–divider-element-spacing:10px;–divider-pattern-height:24px;–divider-pattern-size:20px;–divider-pattern-url:none;–divider-pattern-repeat:repeat-x}.elementor-widget-divider .elementor-divider{display:flex}.elementor-widget-divider .elementor-divider__text{font-size:15px;line-height:1;max-width:95%}.elementor-widget-divider .elementor-divider__element{margin:0 var(–divider-element-spacing);flex-shrink:0}.elementor-widget-divider .elementor-icon{font-size:var(–divider-icon-size)}.elementor-widget-divider .elementor-divider-separator{display:flex;margin:0;direction:ltr}.elementor-widget-divider–view-line_icon .elementor-divider-separator,.elementor-widget-divider–view-line_text .elementor-divider-separator{align-items:center}.elementor-widget-divider–view-line_icon .elementor-divider-separator:after,.elementor-widget-divider–view-line_icon .elementor-divider-separator:before,.elementor-widget-divider–view-line_text .elementor-divider-separator:after,.elementor-widget-divider–view-line_text .elementor-divider-separator:before{display:block;content:””;border-block-end:0;flex-grow:1;border-block-start:var(–divider-border-width) var(–divider-border-style) var(–divider-color)}.elementor-widget-divider–element-align-left .elementor-divider .elementor-divider-separator>.elementor-divider__svg:first-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-left .elementor-divider-separator:before{content:none}.elementor-widget-divider–element-align-left .elementor-divider__element{margin-left:0}.elementor-widget-divider–element-align-right .elementor-divider .elementor-divider-separator>.elementor-divider__svg:last-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-right .elementor-divider-separator:after{content:none}.elementor-widget-divider–element-align-right .elementor-divider__element{margin-right:0}.elementor-widget-divider–element-align-start .elementor-divider .elementor-divider-separator>.elementor-divider__svg:first-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-start .elementor-divider-separator:before{content:none}.elementor-widget-divider–element-align-start .elementor-divider__element{margin-inline-start:0}.elementor-widget-divider–element-align-end .elementor-divider .elementor-divider-separator>.elementor-divider__svg:last-of-type{flex-grow:0;flex-shrink:100}.elementor-widget-divider–element-align-end .elementor-divider-separator:after{content:none}.elementor-widget-divider–element-align-end .elementor-divider__element{margin-inline-end:0}.elementor-widget-divider:not(.elementor-widget-divider–view-line_text):not(.elementor-widget-divider–view-line_icon) .elementor-divider-separator{border-block-start:var(–divider-border-width) var(–divider-border-style) var(–divider-color)}.elementor-widget-divider–separator-type-pattern{–divider-border-style:none}.elementor-widget-divider–separator-type-pattern.elementor-widget-divider–view-line .elementor-divider-separator,.elementor-widget-divider–separator-type-pattern:not(.elementor-widget-divider–view-line) .elementor-divider-separator:after,.elementor-widget-divider–separator-type-pattern:not(.elementor-widget-divider–view-line) .elementor-divider-separator:before,.elementor-widget-divider–separator-type-pattern:not([class*=elementor-widget-divider–view]) .elementor-divider-separator{width:100%;min-height:var(–divider-pattern-height);-webkit-mask-size:var(–divider-pattern-size) 100%;mask-size:var(–divider-pattern-size) 100%;-webkit-mask-repeat:var(–divider-pattern-repeat);mask-repeat:var(–divider-pattern-repeat);background-color:var(–divider-color);-webkit-mask-image:var(–divider-pattern-url);mask-image:var(–divider-pattern-url)}.elementor-widget-divider–no-spacing{–divider-pattern-size:auto}.elementor-widget-divider–bg-round{–divider-pattern-repeat:round}.rtl .elementor-widget-divider .elementor-divider__text{direction:rtl}.e-con-inner>.elementor-widget-divider,.e-con>.elementor-widget-divider{width:var(–container-widget-width,100%);–flex-grow:var(–container-widget-flex-grow)}
Optical Character Recognition
Teramind’s OCR functionality allows you to extract text from images and screenshots, enhancing your monitoring and analysis capabilities.
Website
Monitoring
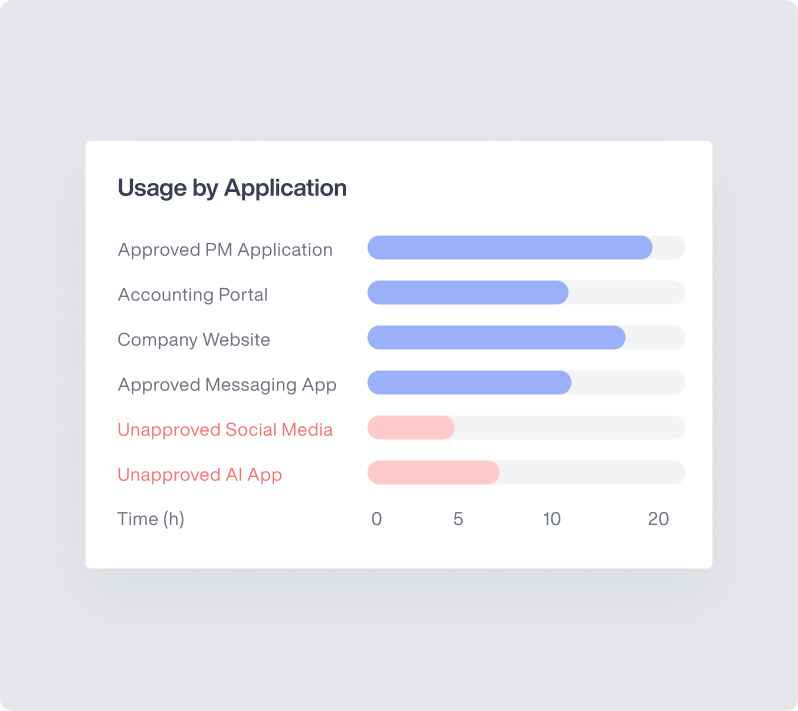
Track employee time spent on websites, identify unproductive web browsing, and enforce company policies with comprehensive website monitoring.
Application
Monitoring
Monitor application usage, track time spent on specific apps, and identify potential security risks with detailed application monitoring on your endpoints.
Email
Monitoring
Monitor employee emails to prevent data leaks, ensure compliance with company policies, and protect sensitive information.
Instant Message Monitoring
Track instant messages and conversations to gain insights into team communication and collaboration, and ensure compliance.
Social Media Monitoring
Monitor social media activity to protect your brand reputation, prevent data leaks, and ensure employees adhere to company policies.
Network
Monitoring
Gain visibility into network activity, identify potential security threats, and optimize network performance with network monitoring.
Citrix
Monitoring
Monitor employee activity within Citrix environments, track application usage, and ensure data security with specialized Citrix monitoring on your devices.
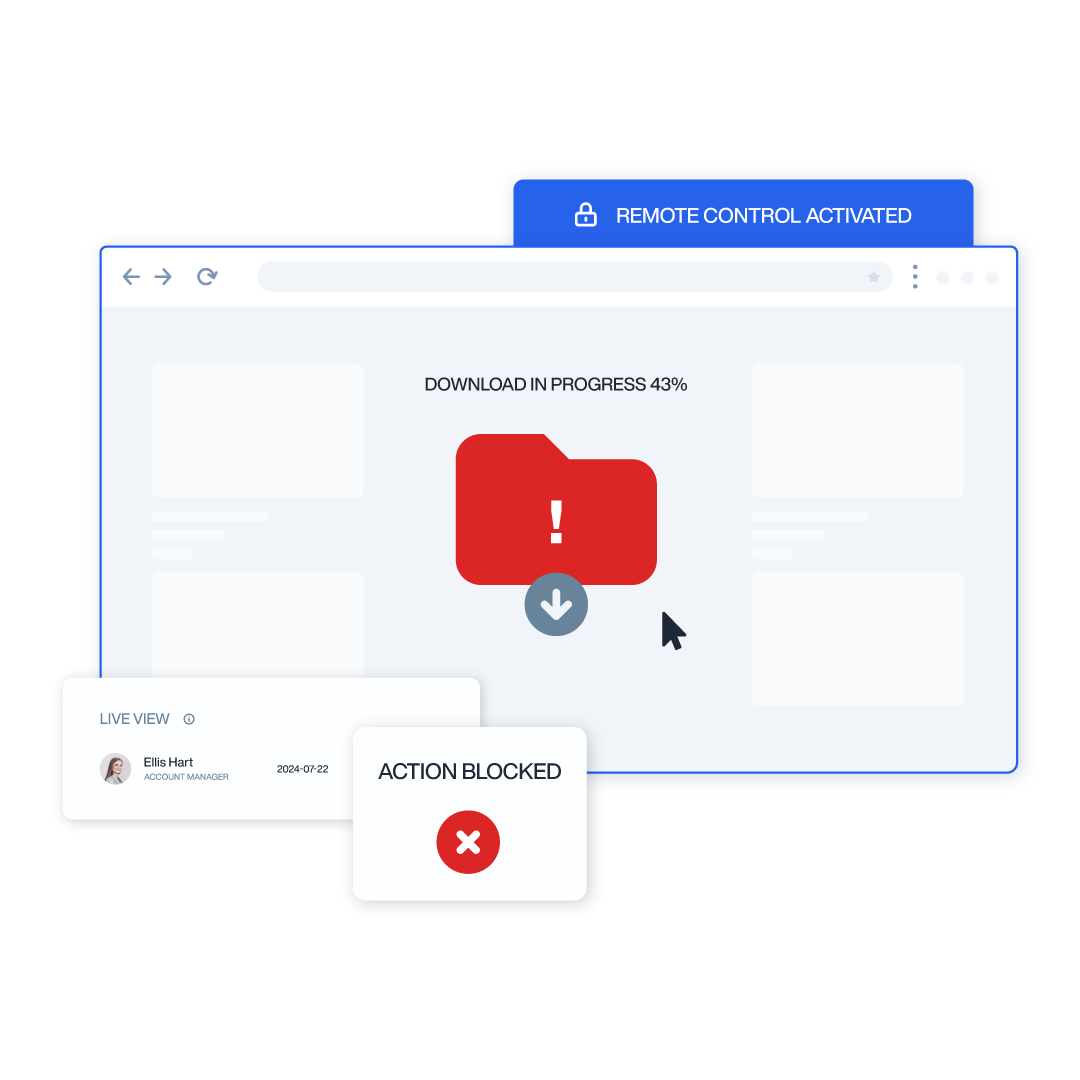
Remote Desktop Control
Take control of remote employee computers in real-time to provide support, troubleshoot issues, or prevent data breaches and insider threats.
RDP Session Recording
Record RDP sessions to gain a comprehensive understanding of user activity, troubleshoot technical problems, and ensure compliance.
Productivity
Analysis
Analyze employee productivity with detailed metrics, identify areas for improvement, and boost productivity across your team members.
Active Vs. Idle
Time Logs
Track active and idle time to understand how employees spend their work hours and optimize time management and productivity.
Unproductive Work
Time Analysis
Identify unproductive work time, analyze patterns, and implement strategies to improve efficiency and time management.
Try Platform
With a Live Demo
to see how it works.

Try Platform
With a Live Demo
to see how it works.

What our Customers Say
“Easy Implementation, Great UI, and amazing product. We leverage Teramind to manage high-risk situations to get in-depth visibility and alerting. It has far surpassed our expectations and has saved us significant data loss.”
.elementor-widget-image-box .elementor-image-box-content{width:100%}@media (min-width:768px){.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper,.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{display:flex}.elementor-widget-image-box.elementor-position-right .elementor-image-box-wrapper{text-align:end;flex-direction:row-reverse}.elementor-widget-image-box.elementor-position-left .elementor-image-box-wrapper{text-align:start;flex-direction:row}.elementor-widget-image-box.elementor-position-top .elementor-image-box-img{margin:auto}.elementor-widget-image-box.elementor-vertical-align-top .elementor-image-box-wrapper{align-items:flex-start}.elementor-widget-image-box.elementor-vertical-align-middle .elementor-image-box-wrapper{align-items:center}.elementor-widget-image-box.elementor-vertical-align-bottom .elementor-image-box-wrapper{align-items:flex-end}}@media (max-width:767px){.elementor-widget-image-box .elementor-image-box-img{margin-left:auto!important;margin-right:auto!important;margin-bottom:15px}}.elementor-widget-image-box .elementor-image-box-img{display:inline-block}.elementor-widget-image-box .elementor-image-box-title a{color:inherit}.elementor-widget-image-box .elementor-image-box-wrapper{text-align:center}.elementor-widget-image-box .elementor-image-box-description{margin:0}
IT Security & Risk Manager
$7B Manufacturing Enterprise
“Cost effective and feature reach DLP and User Behaviour Monitoring Tool. Easy to set up even on-premises. No end-user impact. Cost-effective. Both DLP and User behavior Monitoring.”
IT Manager
$3B Managed Services Provider
“It’s been an amazing experience and a wonderful software that does exactly what you want! Security, control, peace of mind, the ability to know all that is going on in the organization. Very easy to use. It gives you real data! It has given us the protection that we need!”
Renee H
Head of IT Security
FAQs
Can I prevent unauthorized file attachments in emails?
Yes. Attachment monitoring ensures employees do not send unauthorized, sensitive, or confidential files via email. Admins can block unapproved file transfers or quarantine risky attachments.
How does Teramind help businesses stay compliant with regulations?
Teramind maintains comprehensive email logs and audit trails to ensure compliance with GDPR, HIPAA, SOC2, and other industry standards.
Businesses can also generate custom compliance reports for regulatory audits.
Can an employer monitor personal emails sent from a work computer?
Employers can monitor emails sent from company equipment and work email accounts, but they cannot access personal email accounts (e.g., Gmail, Yahoo) without explicit consent.
Can Teramind monitor outbound emails for sensitive data?
Yes. Teramind’s content filtering and keyword alerts flag outbound emails containing classified, sensitive, or personally identifiable information (PII).
Attachment monitoring also prevents unauthorized file transfers.
Can I set up alerts for specific email activities?
Yes. Businesses can configure custom keyword alerts for email communications. Suspicious words, sensitive data, or unauthorized sharing attempts trigger real-time notifications.
.elementor-widget-table-of-contents .elementor-toc__header-title{color:var(–header-color)}.elementor-widget-table-of-contents.elementor-toc–collapsed .elementor-toc__toggle-button–collapse,.elementor-widget-table-of-contents:not(.elementor-toc–collapsed) .elementor-toc__toggle-button–expand{display:none}.elementor-widget-table-of-contents .elementor-widget-container{min-height:var(–box-min-height);border:var(–box-border-width,1px) solid var(–box-border-color,#9da5ae);border-radius:var(–box-border-radius,3px);background-color:var(–box-background-color);transition:min-height .4s;overflow:hidden}.elementor-toc__header{display:flex;align-items:center;justify-content:space-between;padding:var(–box-padding,20px);background-color:var(–header-background-color);border-bottom:var(–separator-width,1px) solid var(–box-border-color,#9da5ae)}.elementor-toc__header-title{font-size:18px;margin:0;color:var(–header-color);flex-grow:1}.elementor-toc__toggle-button{cursor:pointer;display:inline-flex}.elementor-toc__toggle-button i{color:var(–toggle-button-color)}.elementor-toc__toggle-button svg{height:1em;width:1em;fill:var(–toggle-button-color)}.elementor-toc__spinner-container{text-align:center}.elementor-toc__spinner{font-size:2em}.elementor-toc__spinner.e-font-icon-svg{height:1em;width:1em}.elementor-toc__body{padding:var(–box-padding,20px);max-height:var(–toc-body-max-height);overflow-y:auto}.elementor-toc__body::-webkit-scrollbar{width:7px}.elementor-toc__body::-webkit-scrollbar-thumb{background-color:#babfc5;border-radius:10px}.elementor-toc__list-wrapper{list-style:none;padding:0}.elementor-toc__list-item{margin-bottom:.5em}.elementor-toc__list-item.elementor-item-active{font-weight:700}.elementor-toc__list-item .elementor-toc__list-wrapper{margin-top:.5em;margin-inline-start:var(–nested-list-indent,1em)}.elementor-toc__list-item-text{transition-duration:var(–item-text-transition-duration)}.elementor-toc__list-item-text:hover{color:var(–item-text-hover-color);-webkit-text-decoration:var(–item-text-hover-decoration);text-decoration:var(–item-text-hover-decoration)}.elementor-toc__list-item-text.elementor-item-active{color:var(–item-text-active-color);-webkit-text-decoration:var(–item-text-active-decoration);text-decoration:var(–item-text-active-decoration)}.elementor-toc__list-item-text-wrapper{display:flex;align-items:center}.elementor-toc__list-item-text-wrapper:before,.elementor-toc__list-item-text-wrapper i{margin-inline-end:8px;color:var(–marker-color)}.elementor-toc__list-item-text-wrapper svg{margin-inline-end:8px;fill:var(–marker-color);height:var(–marker-size,.5em);width:var(–marker-size,.5em)}.elementor-toc__list-item-text-wrapper i{font-size:var(–marker-size,.5em)}.elementor-toc__list-item-text-wrapper:before{font-size:var(–marker-size,1em)}.elementor-toc–content-ellipsis .elementor-toc__list-item-text{white-space:nowrap;overflow:hidden;text-overflow:ellipsis}.elementor-toc__list-items–collapsible>.elementor-toc__list-wrapper>.elementor-toc__list-item>.elementor-toc__list-wrapper{display:none}.elementor-toc__heading-anchor{position:absolute}.elementor-toc__body .elementor-toc__list-item-text{color:var(–item-text-color);-webkit-text-decoration:var(–item-text-decoration);text-decoration:var(–item-text-decoration);transition-duration:var(–item-text-transition-duration)}.elementor-toc__body .elementor-toc__list-item-text:hover{color:var(–item-text-hover-color);-webkit-text-decoration:var(–item-text-hover-decoration);text-decoration:var(–item-text-hover-decoration)}.elementor-toc__body .elementor-toc__list-item-text.elementor-item-active{color:var(–item-text-active-color);-webkit-text-decoration:var(–item-text-active-decoration);text-decoration:var(–item-text-active-decoration)}ol.elementor-toc__list-wrapper{counter-reset:item}ol.elementor-toc__list-wrapper .elementor-toc__list-item{counter-increment:item}ol.elementor-toc__list-wrapper .elementor-toc__list-item-text-wrapper:before{content:counters(item,”.”) “. “}
Table of Contents
Employee Email Monitoring Explained: How to Stay Secure While Respecting Privacy
Yes, you trust your team— but trust isn’t a security strategy. One accidental CC, one unauthorized attachment, or a single phishing email is all it takes to put your company’s data at risk.
But the challenge here is not ‘technical’; it’s human.
- On one end, your business needs visibility to prevent data breaches, insider threats, and compliance violations.
- On the other, your employees expect privacy and autonomy to do their jobs without feeling like they’re under constant watch.
Striking that balance is tricky. Getting it wrong can lead to legal risks, employee distrust, and regulatory fines you can’t afford. So, where’s the middle ground? Before we get into that, let’s answer your burning question:
Is Employee Email Monitoring Legal?
Short answer — Yes.
However, the ‘legality’ of monitoring your employees’ emails depends on jurisdictional regulations, industry-specific compliance requirements, and what constitutes employer rights vs. employee privacy.
That means, excessive or undisclosed employee monitoring can result in legal liabilities, privacy violations, and reputational damage. Don’t overdo it.
Now to the main topic—
What is Employee Email Monitoring?
Employee email monitoring is the tracking, analyzing, and reviewing of workplace email communications to ensure legal compliance, prevent security threats, detect insider threats, and improve workplace productivity.
This typically involves using employee monitoring software to scan email content, attachments, metadata, and recipient details for policy violations, suspicious activity, or unauthorized data sharing.
Common Methods of Employee Email Monitoring
- Content Filtering and Keyword Analysis. This method scans email subject lines, body text, and attachments for predefined keywords or phrases that indicate potential security risks, compliance violations, or inappropriate communication.
- Traffic and Metadata Analysis. Analyzes data collected from emails such as sender, recipient, time sent, IP addresses, device details, and geolocation. Helps detect suspicious patterns like:
- Bulk outbound emails to external domains.
- Repeated forwarding of company emails.
- Logins from unauthorized locations.
- Attachment Scanning and Data Loss Prevention (DLP). Scans attachments (PDFs, spreadsheets, images) for sensitive data like credit card details, trade secrets, or personal records. Depending on the DLP policy, it can also:
- Block unauthorized file transfers.
- Encrypt sensitive data.
- Quarantine risky emails for review.
- Behavioral Analysis and Anomaly Detection. Uses machine learning to detect deviations from normal email usage, such as sudden spikes in email volume, increased communication with external contacts, or unusual message patterns.
Why Do Companies Monitor Employee Emails?
Ensure Regulatory Compliance
Many industries have strict regulations that require businesses to protect sensitive or confidential information.
Organizations must comply with laws like GDPR, HIPAA, SOX, and FINRA, which mandate how personal and financial data is handled. Email monitoring ensures employees follow these compliance rules by preventing unauthorized sharing of protected information.
For instance, healthcare organizations can detect when patient information is being shared without proper security protocols, preventing costly HIPAA violations. Similarly, financial institutions can track email exchanges to ensure that insider trading regulations are not breached.
Prevent Data Leaks and Insider Threats
Employees handle sensitive company information daily, including financial data, customer records, and intellectual property.
Whether intentional or accidental, an email sent to the wrong recipient or forwarded outside the organization can lead to data leaks. Some employees may also attempt to take confidential information when leaving a company. For example, in 2023, two former Tesla employees leaked the personal information of over 75,000 employees by sharing confidential data with a third party [*].
Monitoring helps detect and prevent cases like this, reducing the risk of disgruntled employees engaging in corporate espionage, insider threats, and accidental exposure.
Prevent Workplace Harassment and Policy Violations
Email communication should remain professional and respectful. However, some employees misuse company email to send inappropriate messages, discriminatory remarks, or harassing content.
Monitoring ensures that workplace policies are followed, helping organizations address violations and maintain a safe and inclusive work environment. It also provides documentation for HR investigations if needed.
Safeguard Intellectual Property and Trade Secrets
Businesses develop proprietary technologies, strategies, and processes that give them a competitive advantage. If employees share this information externally, it can compromise the company’s market position and expose them to legal risks.
Email monitoring helps protect:
- Design specifications and source code: Ensuring product innovations are not leaked before launch.
- Client lists and contract details: Preventing sales teams from taking sensitive client data to competitors.
- Research findings and product roadmaps: Securing valuable intellectual property.
This protection extends beyond deliberate theft to include accidental disclosures that could violate non-disclosure agreements (NDAs) with partners and clients.
Legal and Ethical Considerations in Employee Email Monitoring
Laws governing employee email monitoring vary by country, and businesses must ensure they comply with local, national, and international regulations.
Below are key legal frameworks that impact email monitoring by region and industry:
Compliance Guidelines by Region
European Union: The General Data Protection Regulation (GDPR)
The GDPR sets strict guidelines on how organizations can process and monitor employee data. Under this regulation:
- Employers must justify email monitoring under legitimate interest, legal obligation, or employee consent.
- Monitoring must be necessary and proportionate. Indiscriminate surveillance is illegal.
- Employees have the right to be informed about the extent and purpose of monitoring.
- Companies should conduct a Data Protection Impact Assessment (DPIA) before implementing monitoring practices.
Key Considerations:
- Consent alone is not enough under GDPR—monitoring must meet strict criteria.
- Employers should use pseudonymization or anonymization when possible to minimize privacy risks.
- Countries like France and Germany have additional protections, requiring works council approval before implementing monitoring.
Ethical Implication: Multinational companies must navigate applying different ethical standards across regions, potentially creating ‘unfair’ treatment of employees.
United States: The Electronic Communications Privacy Act (ECPA)
The ECPA (1986) is the primary law governing electronic communications in the workplace. Under this act. It extends government restrictions on wiretaps to include electronic communications, such as emails, phone calls, and other digital transmissions.
Under this law:
- Employers can monitor employee email accounts if there is a legitimate business purpose.
- Monitoring is permitted if employees sign written consent, either explicitly or via company policy.
- The Stored Communications Act (SCA)—a subset (Title II) of ECPA—restricts unauthorized access to stored emails, meaning employers cannot access private email accounts without permission.
Key Considerations:
- Employers should implement a clear, written email monitoring policy that employees acknowledge.
- Many U.S. states have additional privacy laws, such as:
- California’s CCPA, which gives employees the right to know what data is collected.
- Illinois Biometric Information Privacy Act (BIPA), which affects companies that use biometric authentication in email access.
- New York SHIELD Act, which imposes data security requirements, which may impact how monitored emails are stored and protected.
Ethical Implication: In a work-from-home environment, monitoring creates ethical questions about where employer rights end and personal privacy begins.
Canada: The Personal Information Protection and Electronic Documents Act (PIPEDA)
PIPEDA governs private-sector privacy laws in Canada. Under PIPEDA:
- Employers must inform employees about email monitoring and how data is used.
- Monitoring must be reasonable, necessary, and not overly intrusive.
- Employees have the right to access their collected data and request corrections.
Key Considerations:
- In British Columbia and Alberta, additional provincial privacy laws apply, requiring employee consent for monitoring.
- Overly broad or continuous monitoring could be challenged as privacy infringement.
Ethical Implication: PIPEDA reinforces the need for fairness and transparency. Even when employers have the right to monitor, they should set clear boundaries to avoid a perception of excessive surveillance.
Compliance Guidelines by Industry
Beyond regional laws, industry-specific regulations impose additional compliance requirements for email monitoring. Organizations in healthcare, finance, and other regulated sectors must ensure email communications are both monitored for compliance and protected against unauthorized access to prevent legal and financial risks.
Healthcare Sector: Health Insurance Portability and Accountability Act (HIPAA)
HIPAA applies to:
- Healthcare providers, insurers, and business associates handling Protected Health Information (PHI).
- Private companies, including third-party vendors, that process electronic health records (EHRs).
Since email is a primary communication channel, healthcare organizations must ensure that protected health information (PHI) is not improperly shared via email.
Ethical Implication: The sensitivity of patient data means that monitoring must be carefully controlled. It should focus on compliance, not unnecessary surveillance of employee communication.
Financial Sector: Sarbanes-Oxley Act (SOX)
SOX was enacted to prevent corporate fraud and financial misconduct by ensuring transparency in financial reporting.
Email communications often contain critical financial data, which makes email monitoring essential for compliance.
- Financial institutions must monitor and retain email records to prevent fraud and maintain transparency.
- Email records must be protected and retrievable for compliance audits.
- Additional regulations impacting email monitoring in the financial sector include:
- FINRA Rule 3110, which requires financial firms to supervise and retain email communications.
- GLBA (Gramm-Leach-Bliley Act), which mandates encryption and secure email practices when handling customer financial data.
Ethical Implication: Financial institutions must balance compliance monitoring with creating safe channels for legitimate whistleblowing.
Common Challenges in Employee Email Monitoring (+ Solutions)
Employees Feel Their Privacy is Violated
One of the biggest concerns surrounding email monitoring is employee privacy. Many employees perceive email surveillance as an intrusion into their personal space, even when using company equipment.
The fear of being constantly watched creates a culture of mistrust, lower morale, and even reduces productivity and employee engagement.
This issue becomes more complex when employees use company-issued emails for personal matters, such as communicating with family, handling personal finances, or even discussing confidential health matters.
If employees feel like they are under surveillance without justification, resentment may build, leading to disengagement, legal complaints, or high turnover.
Solution: Prioritize Transparency & Communication
- Draft a well-defined employee handbook with ethical guidelines, outlining what is monitored, why, and how the data is used.
- Inform employees upfront and require acknowledgment of the policy. That means providing specific notice in company policies and obtaining written consent from employees before implementing monitoring software.
High Volume of Emails Makes Monitoring Difficult
On any given day, a business might generate thousands or even millions of emails. Manually monitoring this volume is impossible, and even automated tools can struggle to differentiate between genuine threats and harmless messages.
Organizations often face false positives, where legitimate emails are flagged as risky, or false negatives, where real threats go undetected.
This overload of alerts leads to security teams being stretched thin, missing key threats, or wasting time on unnecessary investigations.
Solution: Leverage AI & Automated Threat Detection
- Use advanced monitoring tools with natural language processing (NLP) and machine learning can accurately detect anomalies, suspicious behaviors, and policy violations.
- Define clear monitoring rules to filter emails based on pre-configured keyword alerts, attachments, or metadata.
- Instead of reviewing all emails, monitor only unusual communication patterns (e.g., a sudden increase in email forwarding).
- Fine-tune filters and automation settings to reduce false positives.
Risk of Legal Repercussions for Over-Monitoring
Determining the right scope of monitoring—’what to review and at what frequency?’—can be complex. Too narrow, and you might miss critical incidents. Too broad, and you may breach privacy or get overwhelmed by non-actionable data.
Worse, in many jurisdictions, excessive or undisclosed email monitoring can lead to lawsuits, regulatory fines, and reputational damage.
For example:
- Fines up to $1.5 million per violation (HIPAA)
- Premera Blue Cross agreed to a $6.85 million settlement following a data breach that affected over 10.4 million individuals. The breach was due to a phishing email that allows hackers install malware in Premera’s IT system [*]
- Hefty GDPR penalties (up to 4% of global annual revenue)
- H&M Germany was fined €35.3 million ($41 million) for excessively monitoring employee communications, including emails [*].
- Legal claims from employees for privacy invasion.
- In December 2024, Apple faced a lawsuit from employee Amar Bhakta, who alleged that the company required employees to waive their right to privacy and subjected them to extensive surveillance [*].
Solution: Ensure Compliance with Regional and Industry-Specific Laws
- Adapt your email monitoring strategy based on GDPR, HIPAA, SOX, or ECPA requirements.
- Regularly review your monitoring policies to ensure they remain compliant with regulations.
Employees Find Workarounds (Personal Emails, Shadow IT, External Messaging Apps)
When employees feel restricted by email monitoring, they turn to unapproved communication channels to bypass surveillance.
This includes:
- Using personal email accounts (Gmail, Yahoo) on work devices.
- Switching to encrypted messaging apps like Signal or WhatsApp.
- Using file-sharing services (Google Drive, Dropbox) to send sensitive data externally.
These workarounds create serious security vulnerabilities, as IT teams lose visibility over how private data is shared and who has access. In a recent Gartner report, around 41% of employees use technology that’s not approved by the company [*].
Example: Employees at Finastra used unauthorized cloud storage, exposing 400GB of client data within 24 hours [*].
Solution: Provide Secure, Monitored Alternatives
- Use endpoint security tools to restrict unapproved email and messaging platforms.
- Provide secure, company-approved alternatives like Slack, Microsoft Teams, or Google Workspace with Google Vault for secure archiving.
- Educate employees on the risks of external platforms.
- Track software usage to prevent employees from using unauthorized tools.
Increase in Remote Workforce
With almost every company’s workforce either going remote or hybrid, monitoring employee emails becomes more complex.
Unlike in-office setups where corporate networks and devices are controlled, remote employees may:
- Use personal devices for work emails, leading to a blurry line between personal and professional communication.
- Connect from unsecured networks (public Wi-Fi, home routers), increasing cybersecurity risks.
- Work across different time zones and jurisdictions, where privacy laws vary.
- Develop different work patterns and habits that traditional monitoring systems aren’t calibrated to assess properly.
The distributed nature of this creates significant blind spots in traditional security frameworks designed for centralized office environments. This makes it difficult to monitor remote employees without being intrusive.
Solution: Set Up A Zero-Trust Security Framework
- Require multi-factor authentication (MFA) for all email logins, preventing unauthorized access even if credentials are compromised.
- Mandate the use of encrypted VPN tunnels to prevent man-in-the-middle attacks and ensure email traffic is protected on untrusted networks (e.g., public Wi-Fi).
- Utilize monitoring tools specifically designed to monitor remote employees without excessive GPS tracking or webcam recording.
Best Practices: How to Implement Employee Email Monitoring Effectively
Create a Clear Email Monitoring Policy That Employees Understand
Before implementing email monitoring, organizations must define, document, and communicate a well-structured policy that outlines:
- What is being monitored (e.g., content, attachments, metadata, recipient domains) and what is not (personal communications on approved channels).
- Why monitoring is necessary (e.g., security, compliance, insider threat detection).
- Who has access to monitored data (e.g., HR teams only).
- How long email records are retained and under what circumstances they are reviewed.
Best Practice:
- Integrate the policy into onboarding materials and periodic security training to ensure employees are fully aware of monitoring practices.
- Allow employees to request access to their own monitored data (where legally possible) to maintain accountability.
Implement Role-Based Monitoring & Least Privilege Access
Not all employees pose the same level of risk. As such, monitoring should be proportional to security needs. Over-monitoring low-risk employees wastes resources and can violate privacy rights, while failing to monitor high-risk roles creates security vulnerabilities.
The best way to do this is classifying employees by risk level:
- High-Risk Roles (Executives, Finance, Legal, HR, IT Admins). Require stricter monitoring due to access to financial data, trade secrets, and sensitive employee records.
- Standard Employees. General security monitoring, focusing on preventing external threats and phishing attacks.
- Privileged IT/Admin Accounts. Continuous monitoring is essential due to elevated access rights and insider threat risks.
Additionally, limit access to email monitoring logs using least privilege access (LPA) principles to prevent misuse or unauthorized access.
Best Practice:
- Avoid broad surveillance—target only high-risk behaviors.
- Apply access control: Limit who can view, analyze, and act on monitored data.
Monitor External Email Communications & Unauthorized Data Transfers
One of the biggest security risks is employees intentionally or accidentally sending company data to external recipients. Without proper controls, sensitive information can be leaked, stolen, or misused.
Here’s what to do:
- Block unauthorized auto-forwarding to personal email accounts (e.g., Gmail, Yahoo).
- Monitor outgoing emails and attachments employees send to external domains.
- Use DLP tools to detect and block sensitive attachments from leaving the company network (e.g.,files or emails with keywords containing “confidential,” “wire transfer,” “SSN”).
- Enforce redaction and encryption for emails containing financial records, legal documents and Personal Identifiable Information (PII).
Best Practice:
- Instead of blocking legitimate emails, use sandboxing technology that opens and scans email content in a secure virtual environment before delivering it.
Educate Employees to Reduce Email Risks and Compliance Violations
Employees often see email monitoring as intrusive unless they understand its purpose. Education is key to preventing resistance.
Here’s what the training should cover:
- Safe email practices: How to spot phishing emails, avoid risky attachments, and verify senders.
- Acceptable use policy: What’s considered professional and inappropriate in workplace communication.
- Compliance obligations: How email monitoring helps maintain industry regulations (GDPR, HIPAA, etc.).
Best Practice:
- Conduct quarterly security awareness sessions to reinforce best practices.
- Encourage employees to report suspicious emails instead of fearing punishment.
Regularly Audit & Review Monitoring Policies
Monitoring policies must evolve as threats, compliance requirements, and business needs change. Regular audits help fine-tune monitoring settings, ensure compliance, and minimize unnecessary surveillance.
Here’s what to do:
- Adjust monitoring based on evolving threats (e.g., new phishing techniques, insider fraud trends).
- Get legal reviews to ensure compliance with local and global regulations.
- Allow employee feedback channels to address concerns and improve transparency.
Best Practice:
- Run conduct controlled simulations where an internal security team mimics insider threats to test email monitoring effectiveness. This helps you analyze how well monitoring tools detect policy violations, data leaks, or unauthorized access attempts.
Control What Matters. Protect What’s Important.
The truth is, you don’t want to micromanage every email. You don’t have the time, and your employees don’t want to feel like they’re under a microscope. But at the same time, you can’t afford to leave your business exposed to external attacks, insider threats, or compliance risks.
So, what you really need is a solution that does three things:
- Visibility without surveillance,
- Security without overreach, and
- Control without disrupting productivity.
And that’s exactly what Teramind delivers.
- Stops Data Leaks Before They Cost You: Accidental or a deliberate leak? Doesn’t matter. Teramind keeps you ahead of the risk by detecting unauthorized sharing, suspicious attachments, or policy violations before they turn into real problems.
- Makes Compliance Simple and Stress-Free: From GDPR to HIPAA, regulatory fines aren’t just expensive, they can cripple your business. Instead of leaving compliance to chance, Teramind ensures that sensitive data stays protected, automatically flagging risks so you don’t have to scramble when auditors come knocking.
- Empowers Your Team Without Disrupting Work: Security shouldn’t come at the cost of efficiency. Unlike rigid, invasive monitoring tools, Teramind works quietly in the background, ensuring employees can do their jobs without unnecessary restrictions.
Security and trust should go hand in hand. With Teramind, they finally can.
The post New – Email Monitoring first appeared on Teramind.
Source: itsecuritycentral.teramind.co

